Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article lists recent features added for unified security operations in the Microsoft Defender portal.
August 2025
- Viewing unified RBAC in multitenant management to GA
- Tenant groups in multitenant management renamed to distribution profiles
- Distribute Microsoft Defender for Endpoint security policies with multitenant management
Viewing unified RBAC in multitenant management to GA
Viewing unified role-based access control (RBAC) in the Microsoft Defender multitenant management portal is now generally available. This feature allows you to view a comprehensive view of permissions and access for your tenants.
Creating and editing custom roles remains in preview. For more information, see Manage unified role-based access control in multitenant management.
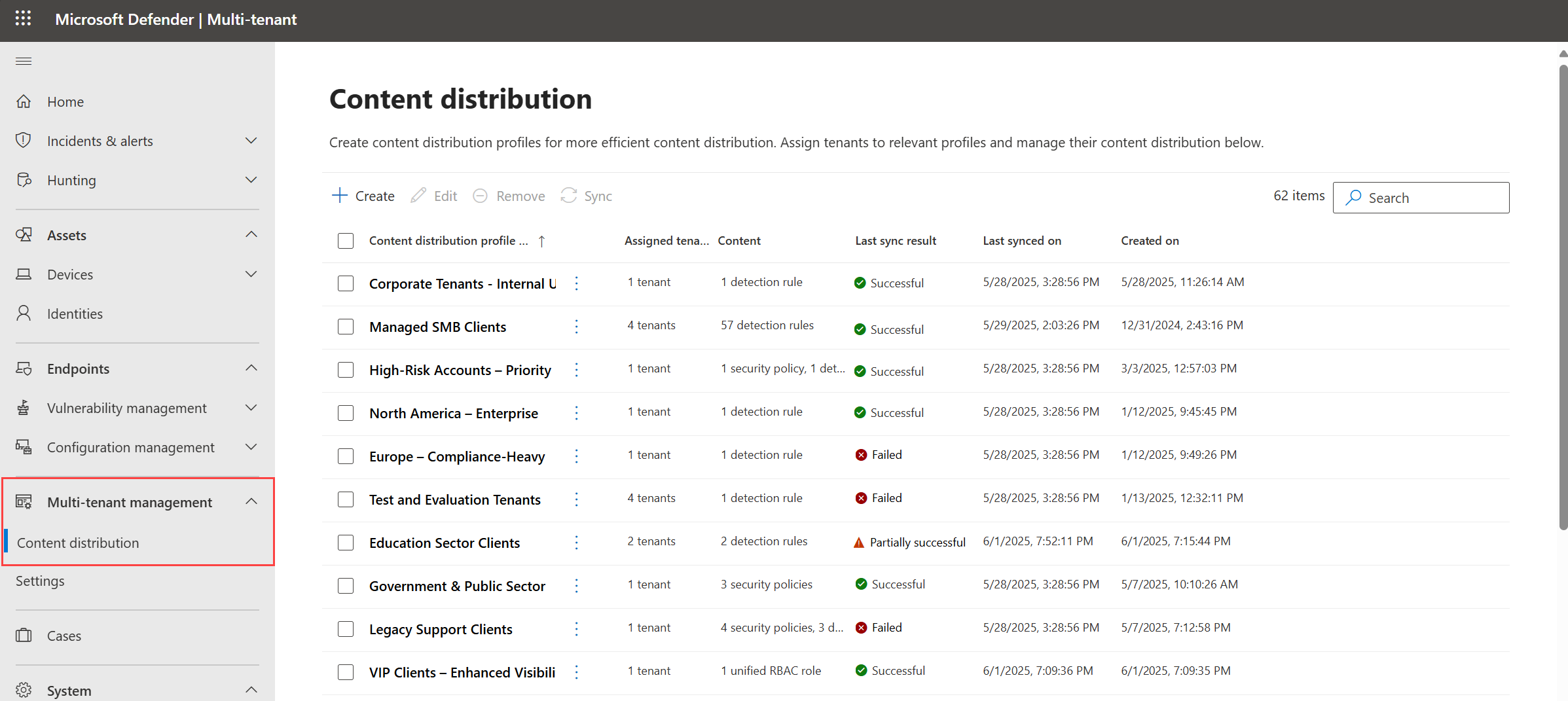
Tenant groups in multitenant management renamed to distribution profiles
In the multitenant portal, tenant groups are now renamed to content distribution profiles.
Functionality remains the same: Content distribution profiles enable you to distribute security content, including custom detection rules and endpoint security policies, at scale across all of your tenants, based on categories like business groups or location. For example:
For more information, see Content distribution using distribution profiles in multitenant management.
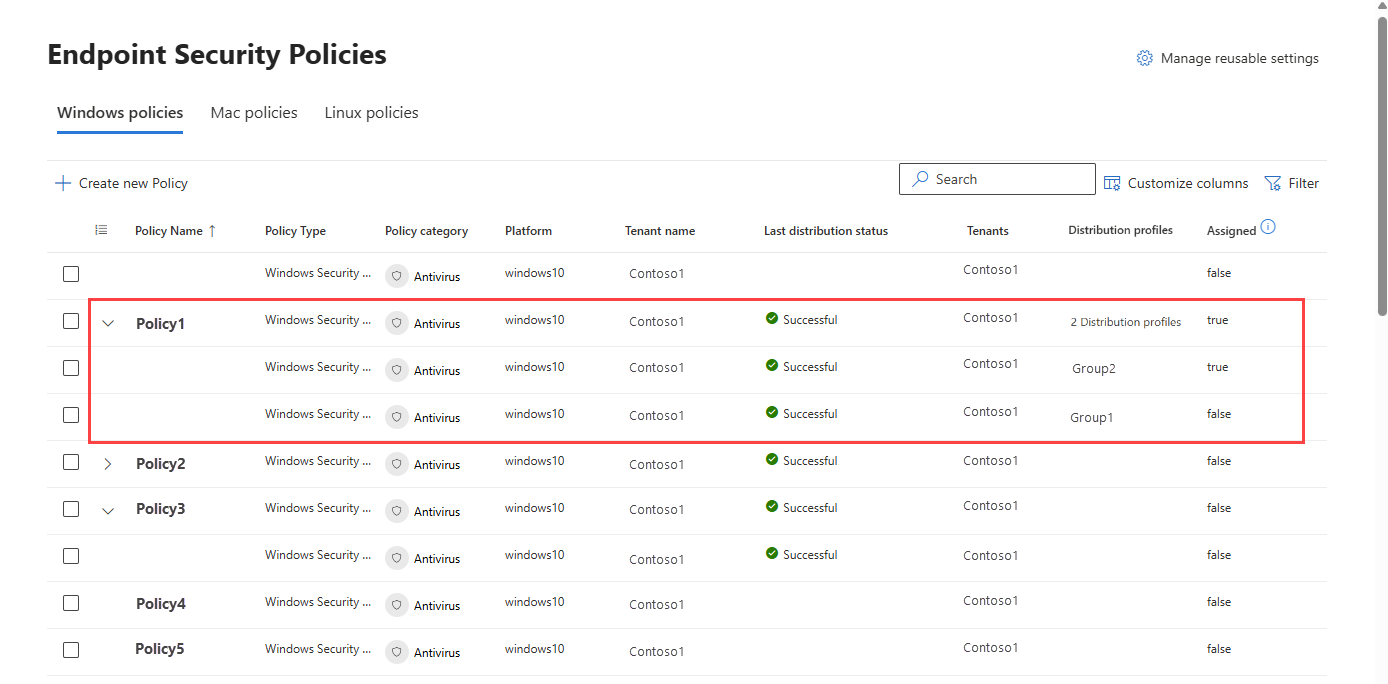
Distribute Microsoft Defender for Endpoint security policies with multitenant management
Microsoft Defender for Endpoint security policies can now be distributed as content across multiple tenants using the Defender multitenant portal, empowering security teams to manage endpoint security policies at scale. Distributed policies are shown in the Configuration management > Endpoint security policies page in a hierarchical view so that you can identify parent policies and their distributed copies across tenants.
The original policy’s page also shows the overall distribution status and lists recipient tenants and distribution profiles.
For more information, see Endpoint security policies in multitenant management and Content distribution in multitenant management.
July 2025
- For new customers only: Automatic onboarding and redirection to the Microsoft Defender portal
- No limit on the number of workspaces you can onboard to the Defender portal
- Microsoft Sentinel in the Azure portal to be retired July 2026
For new customers only: Automatic onboarding and redirection to the Microsoft Defender portal
For this update, new Microsoft Sentinel customers are customers who are onboarding the first workspace in their tenant to Microsoft Sentinel after July 1, 2025.
Starting on July 1 2025, such new customers who are also:
- not Azure Lighthouse-delegated users and
- who have the permissions of a subscription Owner or a User access administrator
Have their workspaces automatically onboarded to the Defender portal together with onboarding to Microsoft Sentinel. Users of such workspaces, who also aren't Azure Lighthouse-delegated users, see links in Microsoft Sentinel in the Azure portal that redirect them to the Defender portal.
For example:
Such users use Microsoft Sentinel in the Defender portal only.
New customers who don't have relevant permissions aren't automatically onboarded to the Defender portal, but they do still see redirection links in the Azure portal, together with prompts to have a user with relevant permissions manually onboard the workspace to the Defender portal.
This change streamlines the onboarding process and ensures that new customers can immediately take advantage of unified security operations capabilities without the extra step of manually onboarding their workspaces.
For more information, see:
- Onboard Microsoft Sentinel
- Microsoft Sentinel in the Microsoft Defender portal
- Changes for new customers
No limit on the number of workspaces you can onboard to the Defender portal
There is no longer any limit to the number of workspaces you can onboard to the Defender portal.
Limitations still apply to the number of workspaces you can include in a Log Analytics query, and in the number of workspaces you can or should include in a scheduled analytics rule.
For more information, see:
- Connect Microsoft Sentinel to the Microsoft Defender portal
- Multiple Microsoft Sentinel workspaces in the Defender portal
- Extend Microsoft Sentinel across workspaces and tenants
Microsoft Sentinel in the Azure portal to be retired July 2026
Microsoft Sentinel is generally available in the Microsoft Defender portal, including for customers without Microsoft Defender XDR or an E5 license. This means that you can use Microsoft Sentinel in the Defender portal even if you aren't using other Microsoft Defender services.
Starting in July 2026, Microsoft Sentinel will be supported in the Defender portal only, and any remaining customers using the Azure portal will be automatically redirected.
If you're currently using Microsoft Sentinel in the Azure portal, we recommend that you start planning your transition to the Defender portal now to ensure a smooth transition and take full advantage of the unified security operations experience offered by Microsoft Defender.
For more information, see:
- Microsoft Sentinel in the Microsoft Defender portal
- Transition your Microsoft Sentinel environment to the Defender portal
- Planning your move to Microsoft Defender portal for all Microsoft Sentinel customers (blog)
June 2025
Case management now generally available in the Defender multitenant portal
The Microsoft Defender portal's case management feature is now generally available in the Defender multitenant portal. For more information, see View and manage cases across multiple tenants in the Microsoft Defender multitenant portal.
May 2025
- Unified role-based access control in multitenant portal (Preview)
- All Microsoft Sentinel use cases generally available in the Defender portal
- Case management now available for the Defender multitenant portal (Preview)
Unified role-based access control in multitenant management (Preview)
Unified role-based access control (URBAC) is now available in the Microsoft Defender multitenant management portal. You can create, delete, import, and edit roles in the multitenant management portal. This capability provides a comprehensive view of permissions and access for your tenants, and a centralized administration to manage these permissions.
For more information, see Manage unified role-based access control in multitenant management.
All Microsoft Sentinel use cases generally available in the Defender portal
All Microsoft Sentinel use cases that are in general availability, including multi-tenant and multi-workspace capabilities and support for all government and commercial clouds, are now also supported for general availability in the Defender portal.
We recommend that you onboard your workspaces to the Defender portal to take advantage of a single location for all your security operations. For more information, see:
- The Best of Microsoft Sentinel - now in Microsoft Defender (blog)
- Transition your Microsoft Sentinel environment to the Defender portal
- Microsoft Sentinel in the Microsoft Defender portal
Case management now available for the Defender multitenant portal (Preview)
SecOps teams for large organizations and managed security service providers (MSSPs) must manage cases across multiple tenants. This can now be done without leaving the Defender multitenant portal.
For more information, see View and manage cases across multiple tenants in the Microsoft Defender multitenant portal.
April 2025
- Merge incidents manually (Preview)
- Multi workspace and multi tenant support for Microsoft Sentinel (Preview)
- Case management now generally available
Merge incidents manually (Preview)
If two incidents should be merged because they describe the same attack story, but aren't merged for any of the reasons listed in "When incidents aren't merged", you can now merge the incidents manually after you fix the underlying reasons.
For example, if the incidents weren't merged because they were assigned to two different people, you can remove the assignment of one of the incidents and then merge the incidents manually.
To understand more about merging incidents, see Alert correlation and incident merging in the Microsoft Defender portal.
For instructions on merging incidents manually, see Merge incidents manually in the Microsoft Defender portal.
Multi workspace and multi tenant support for Microsoft Sentinel (Preview)
Microsoft Sentinel now supports multiple workspaces in the Defender portal, using one primary workspace per tenant and multiple secondary workspaces.
A primary workspace's alerts are correlated with Defender XDR data, which results in incidents that include alerts from Microsoft Sentinel's primary workspace and Defender XDR. All other onboarded workspaces are considered secondary workspaces. Incidents are created based on the workspace’s data and won't include Defender XDR data.
If you're working with multiple tenants and multiple workspaces per tenant, you can also use Microsoft Defender multitenant management to view incidents and alerts, and to hunt for data in Advanced hunting, across both multiple workspaces and tenants.
For more information, see:
- Multiple Microsoft Sentinel workspaces in the Defender portal
- Connect Microsoft Sentinel to the Microsoft Defender portal
- Microsoft Defender multitenant management
- View and manage incidents and alerts in Microsoft Defender multitenant management
- Advanced hunting in Microsoft Defender multitenant management
Cross-cloud multitenant management (Preview)
Multitenant management in Microsoft Defender now supports managing tenants in other Microsoft cloud environments. Security operations teams operating in government cloud environments can now manage their entire security operations, including tenants in other Microsoft cloud environments, in a single pane of glass. For more information, see Manage tenants in other Microsoft cloud environments.
Case management now generally available
The Microsoft Defender portal's case management feature is now generally available. For more information, see Manage security operations cases natively in the Microsoft Defender portal.
January 2025
- Unified threat intelligence
- Manage SecOps work natively with case management (Preview)
- Unified device timeline in Microsoft Defender portal (Preview)
- SOC optimization updates for unified coverage management
Unified threat intelligence
Microsoft Sentinel-powered threat intelligence has moved in the Defender portal to Intel management, unifying threat intelligence features. In the Azure portal, the location remains unchanged.
Along with the new location, the management interface streamlines the creation and curation of threat intel with these key features:
- Define relationships as you create new STIX objects.
- Curate existing threat intelligence with the new relationship builder.
- Create multiple objects quickly by copying common metadata from a new or existing TI object with the duplicate feature.
- Use advanced search to sort and filter your threat intelligence objects without even writing a Log Analytics query.
For more information, see the following articles:
- Uncover adversaries with threat intelligence across the Defender portal
- New STIX objects in Microsoft Sentinel
- Understand threat intelligence
Case management (Preview)
Case management is the first installment of an end-to-end solution that provides seamless management of your security work. SecOps teams maintain security context, work more efficiently and respond faster to attacks when they manage case work without leaving the Defender portal. Here's the initial set of scenarios and features that case management supports.
- Define your own case workflow with custom status values
- Assign tasks to collaborators and configure due dates
- Handle escalations and complex cases by linking multiple incidents to a case
- Manage access to your cases using RBAC
This is just the start. Stay tuned for additional capabilities as we evolve this solution.
For more information, see the following articles:
- Manage security operations cases natively in the Microsoft Defender portal
- Microsoft Sentinel blog - Improve SecOps collaboration with case management
Unified device timeline in Microsoft Defender portal (Preview)
The unified device timeline, a single, cohesive view that integrates device activity from Microsoft Sentinel and Defender XDR into a single timeline, is now available in Preview. This feature streamlines security investigations by enabling analysts to access all relevant device activities in one place, reducing the need to switch between platforms and lowering incident response times.
For more information, see Device entity page in Microsoft Defender.
SOC optimization updates for unified coverage management
In workspaces enabled for unified security operations, SOC optimizations now support both SIEM and XDR data, with detection coverage from across Microsoft Defender services.
In the Defender portal, the SOC optimizations and MITRE ATT&CK pages also now provide extra functionality for threat-based coverage optimizations to help you understand the impact of the recommendations on your environment and help you prioritize which to implement first.
Enhancements include:
| Area | Details |
|---|---|
| SOC optimizations Overview page | - A High, Medium, or Low score for your current detection coverage. This sort of scoring can help you decide which recommendations to prioritize at a glance. - An indication of the number of active Microsoft Defender products (services) out of all available products. This helps you understand whether there's a whole product that you're missing in your environment. |
| Optimization details side pane, shown when you drill down to a specific optimization |
- Detailed coverage analysis, including the number of user-defined detections, response actions, and products you have active. - Detailed spider charts that show your coverage across different threat categories, for both user-defined and out-of-the-box detections. - An option to jump to the specific threat scenario in the MITRE ATT&CK page instead of viewing MITRE ATT&CK coverage only in the side pane. - An option to View full threat scenario to drill down to even further details about the security products and detections available to provide security coverage in your environment. |
| MITRE ATT&CK page | - A new toggle to view coverage by threat scenario. If you've jumped to the MITRE ATT&CK page from either a recommendation details side pane or from the View full threat scenario page, the MITRE ATT&CK page is pre-filtered for your threat scenario. - The technique details pane, shown on the side when you select a specific MITRE ATT&CK technique, now shows the number of active detections out of all available detections for that technique. |
For more information, see Optimize your security operations and Understand security coverage by the MITRE ATT&CK framework.
December 2024
- New SOC optimization recommendations based on similar organizations (Preview)
- Microsoft Sentinel workbooks now available to view directly in the Microsoft Defender portal
New SOC optimization recommendations based on similar organizations (Preview)
SOC optimizations now include new recommendations for adding data sources to your workspace based on the security posture of other organizations in similar industries and sectors as you, and with similar data ingestion patterns.
For more information, see SOC optimization reference of recommendations.
Microsoft Sentinel workbooks now available to view directly in the Microsoft Defender portal
Microsoft Sentinel workbooks are now available for viewing directly in the Microsoft Defender portal. Now, in the Defender portal, when you select Microsoft Sentinel > Threat management > Workbooks, you remain in the Defender portal instead of a new tab being opened for workbooks in the Azure portal. Continue tabbing out to the Azure portal only when you need to edit your workbooks.
Microsoft Sentinel workbooks are based on Azure Monitor workbooks, and help you visualize and monitor the data ingested to Microsoft Sentinel. Workbooks add tables and charts with analytics for your logs and queries to the tools already available.
For more information, see Visualize and monitor your data by using workbooks in Microsoft Sentinel and Connect Microsoft Sentinel to Microsoft Defender XDR.
Related content
For more information on what's new with other Microsoft Defender security products and Microsoft Sentinel, see:
- What's new in Microsoft Sentinel
- What's new in Microsoft Defender XDR
- What's new in Microsoft Defender for Office 365
- What's new in Microsoft Defender for Endpoint
- What's new in Microsoft Defender for Identity
- What's new in Microsoft Defender for Cloud Apps
- What's new in Microsoft Security Exposure Management
You can also get product updates and important notifications through the message center.