Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In this article, you learn how to manage workspace access tokens in Playwright Workspaces. You use access tokens to authenticate and authorize access to your workspace.
Access tokens are associated with a user account and workspace. When you use an access token for running Playwright tests, the service checks your Azure role-based access control (Azure RBAC) role to verify if you're granted access to run tests on the service. Learn more about workspace access in Playwright Workspaces.
You can create multiple access tokens per workspace, for example to distinguish between running tests interactively or as part of your continuous integration (CI) workflow. When you create an access token, the token has a limited lifespan.
Important
Playwright Workspaces is currently in preview. For legal terms that apply to Azure features that are in beta, in preview, or otherwise not yet released into general availability, see the Supplemental Terms of Use for Microsoft Azure Previews.
Prerequisites
- An Azure account with an active subscription. Create an account for free.
- A Playwright workspace. To create a workspace, see Quickstart: Run Playwright tests at scale.
- To create or delete access tokens, your Azure account needs to have the Contributor or Owner role at the workspace level. Learn more about managing access to a workspace.
Protect your access tokens
Your workspace access tokens are similar to a password for your Playwright workspace. Always be careful to protect your access tokens. Avoid distributing access tokens to other users, hard-coding them, or saving them anywhere in plain text that is accessible to others.
Revoke and recreate your tokens if you believe they may have been compromised.
Enable authentication using access tokens
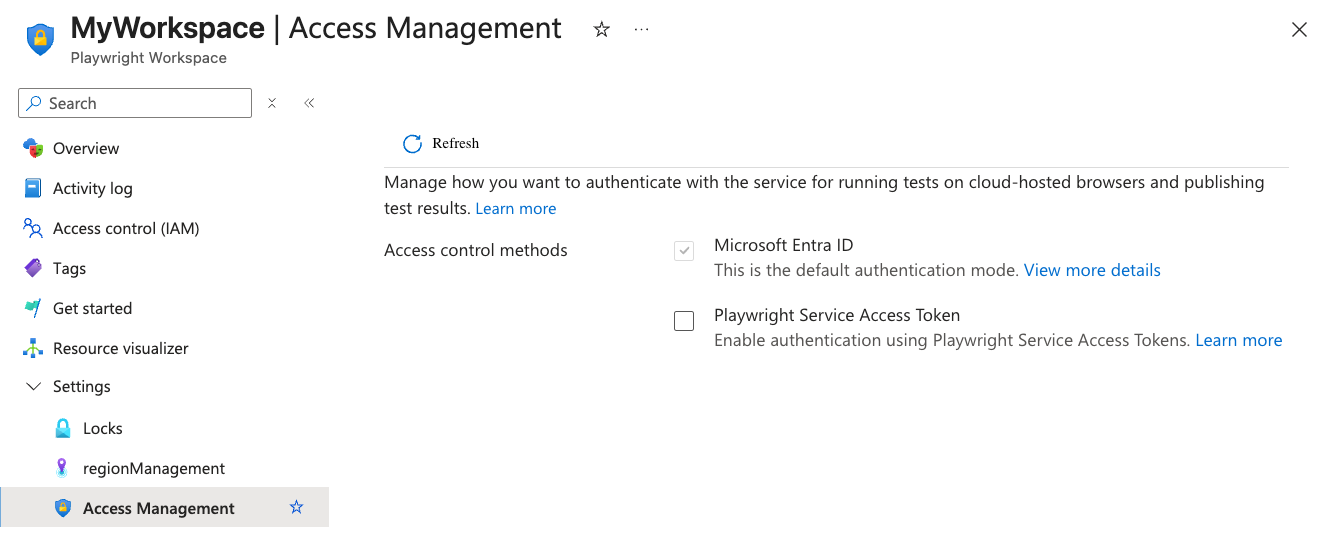
By default, Playwright Workspaces uses Microsoft Entra ID for authentication, which is the recommended approach. Although access token authentication is supported, it is disabled by default because it is less secure. To use access tokens, you must explicitly enable this option for your workspace.
Caution
Your workspace access tokens are similar to a password for your Playwright workspace. Always be careful to protect your access tokens. Avoid distributing access tokens to other users, hard-coding them, or saving them anywhere in plain text that is accessible to others. Revoke and recreate your tokens if you believe they are compromised.
To enable authentication using access tokens:
Sign in to the Azure portal with your Azure account and navigate to your workspace.
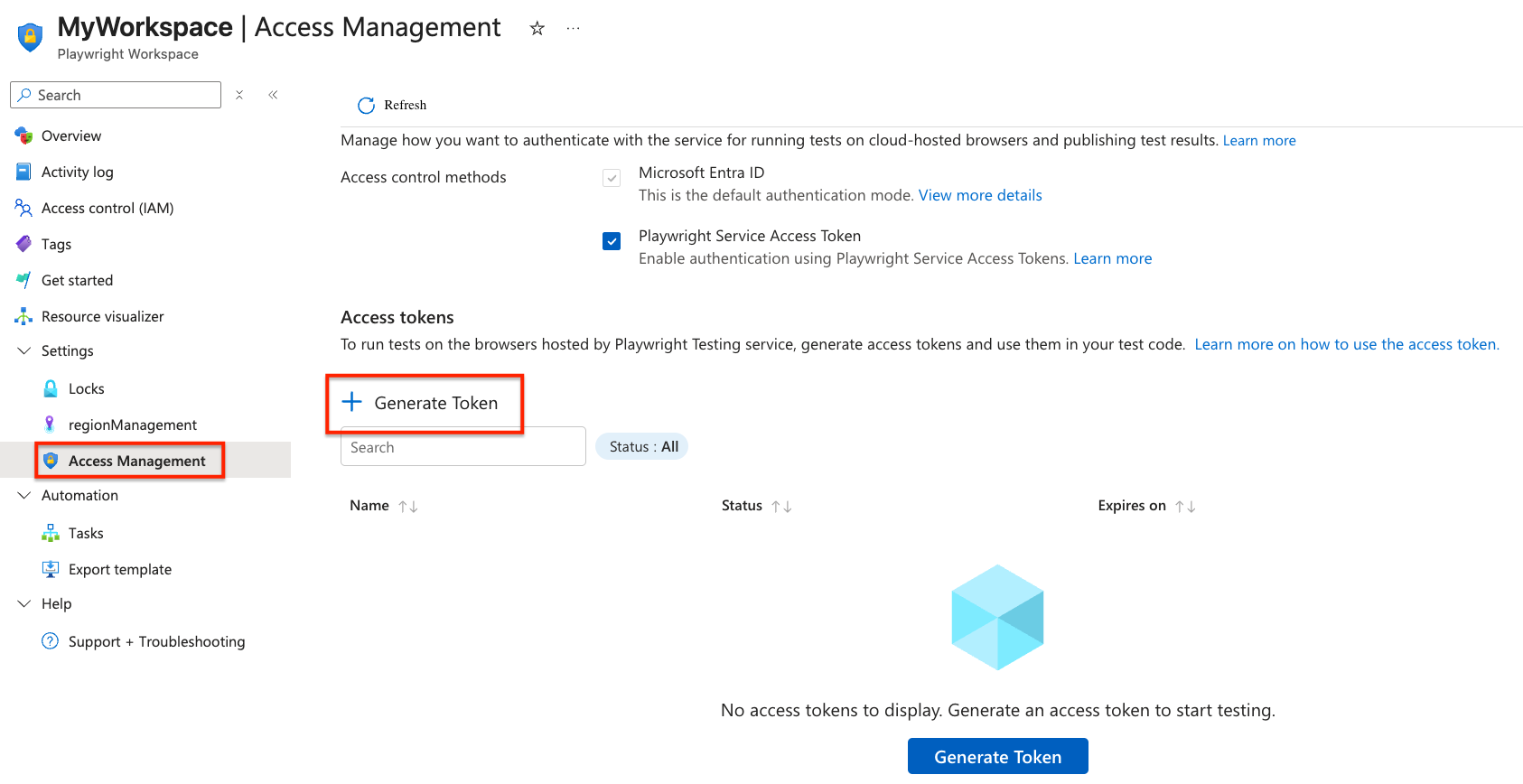
In the Settings section, select Access Management.
Check the box for Playwright Service Access Token to enable it.
Caution
Authentication using access tokens is less secure. Learn how to manage access tokens
View all workspace access tokens
You can view the list of access tokens for your workspace in the Azure portal. For each token, the list displays the token name, status, and expiration date. You can't retrieve the access token value after it has been created.
You can only view the list of access tokens for the workspaces you have access to.
To view the list of workspace access tokens:
Sign in to the Azure portal with your Azure account and navigate to your workspace.
In the Settings section, select Access Management.
If the Playwright Service Access Token option is checked, the page will list all access tokens for the workspace.
Generate a workspace access token
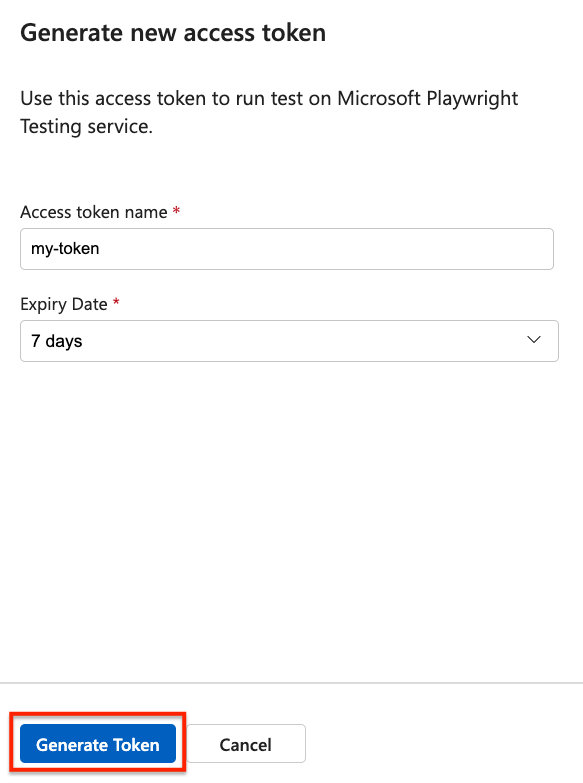
Create an access token to authorize access to your Playwright workspace, and to run existing Playwright tests in your workspace. You can create multiple access tokens for your workspace. When you create an access token, you have to specify an expiration date for the token. After a token expires, you need to create a new access token.
When you use an access token, the service checks the Azure RBAC role of the user that is associated with the access token to verify that the required permissions are granted. For example, if you have the Reader role, you can't run Playwright tests but you can view the test results. When there are role assignment changes, the service checks the permissions at the time you perform the action.
To create a new workspace access token:
Sign in to the Azure portal with your Azure account and navigate to your workspace.
In the Settings section, select Access Management.
On the Access Management page, select Generate token.
Enter the access token details, and then select Generate token.
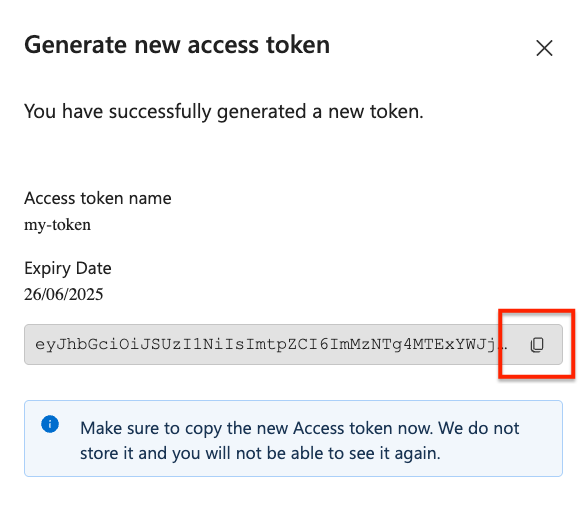
Copy the access token for the workspace.
You can save the access token in a CI/CD secrets store or use it in an environment variable for running tests interactively.
Important
You can only access the token value immediately after you've created it. You can't access the token value anymore at a later time.
Note
The number of access tokens per user and per workspace is limited. For more information, see the Playwright Workspaces limits.
Delete an access token
You can only delete access tokens that you created in a workspace. To create an access token:
Sign in to the Azure portal with your Azure account and navigate to your workspace.
In the Settings section, select Access Management.
If the Playwright Service Access Token option is checked, the page will list all access tokens for the workspace.
Select Delete next to the access token that you want to delete.
Select Delete on the deletion confirmation page.
Caution
You can't undo the delete operation of an access token. Any existing scripts for running tests with this token will fail after deleting the access token.
Related content
- Learn more about managing access to a workspace.
- Learn more about managing authentication to the workspace