Describe the Threat Intelligence Briefing Agent
Threat intelligence analysts often face challenges in delivering actionable intelligence due to the time-consuming processes of collecting, filtering, and analyzing data from various sources. These delays can make reports obsolete as threats evolve rapidly.
The Threat Intelligence Briefing Agent addresses these challenges by applying dynamic automation and deep generative AI to produce customized, context-rich reports within minutes. It integrates signals from tools like Microsoft Defender External Attack Surface Management and Microsoft Defender for Endpoint to provide situational awareness for CISOs and managers, while offering a solid foundation for analysts to enhance threat defense strategies.
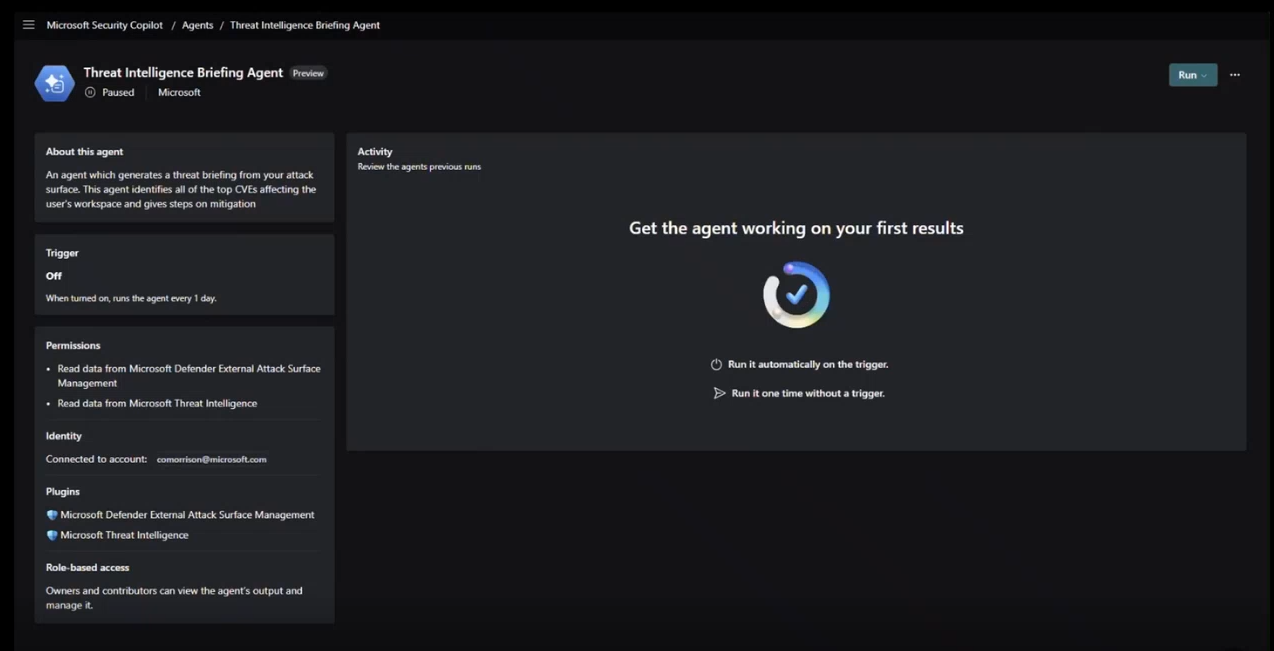
Information about the agent and prerequisites
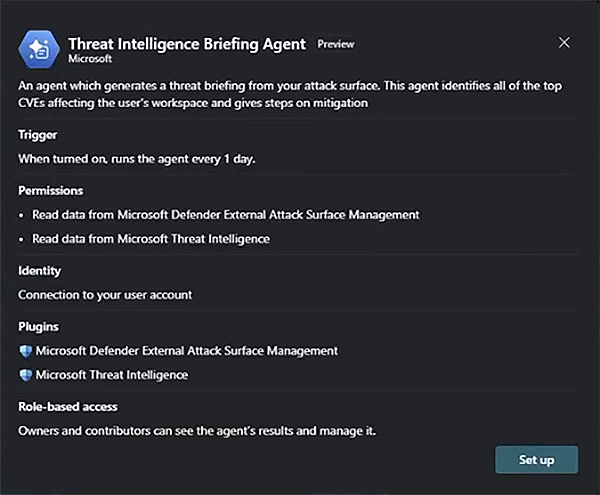
The Threat Intelligence Briefing Agent, which is available through the standalone experience in Security Copilot, is characterized as follows:
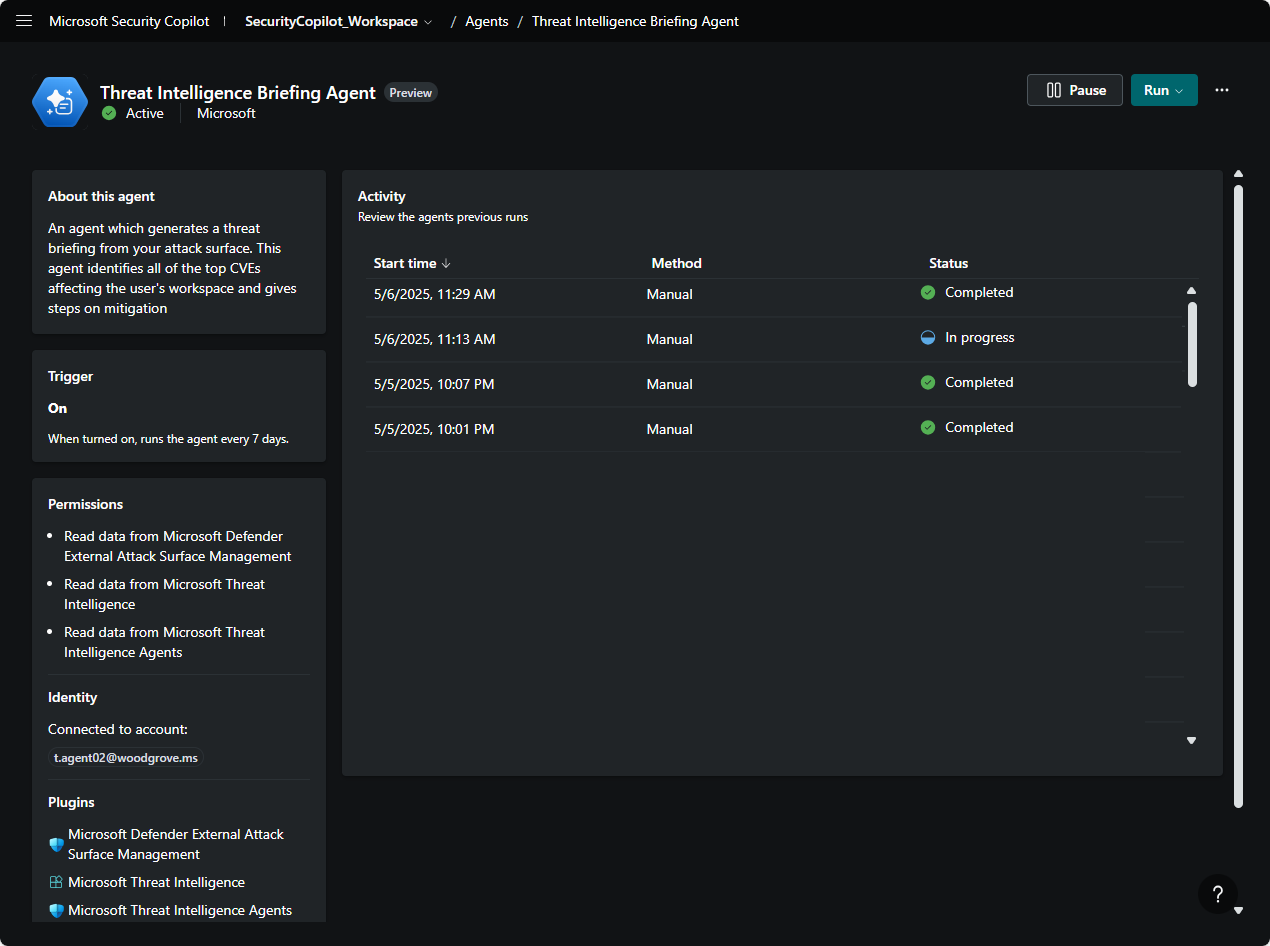
- Trigger: The agent can be triggered manually or set to run at scheduled intervals.
- Permissions: This agent can read data from Defender External Attack Surface Management and Defender Vulnerability Management.
- Identity: Connection to an existing user account.
- Products: Microsoft Security Copilot with provisioned capacity is necessary to run the agent.
- Plugins: The Microsoft Threat Intelligence plugin is mandatory, while optional plugins like Defender External Attack Surface Management and Defender Vulnerability Management add more context to the output.
- Role-based access: Owners and contributors can view generated reports within the agent library page.
Set up
Follow these steps to configure the Threat Intelligence Briefing Agent, corresponding images are shown in the tabbed images that follow:
- Agents - Navigate to the Agents page in the Microsoft Security Copilot portal and select View details under the Threat Intelligence Briefing Agent.
- Details page - Review the agent details and select Set up.
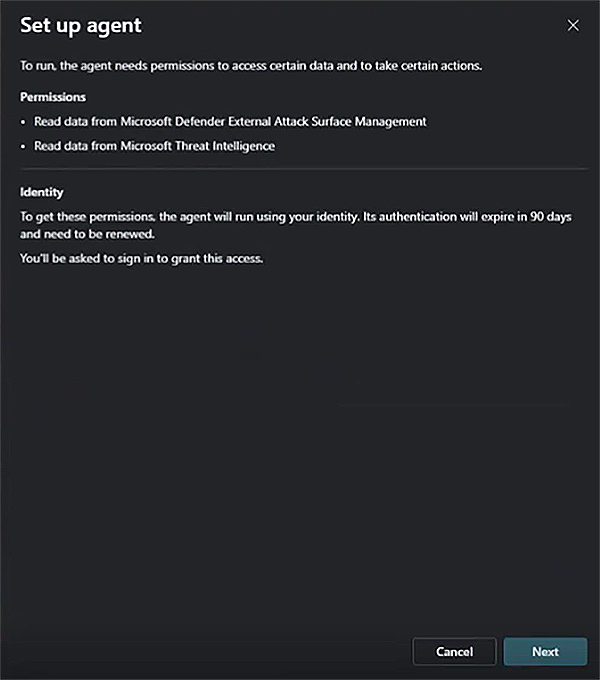
- Set up - Connect a user account by selecting Next and choosing the appropriate account.
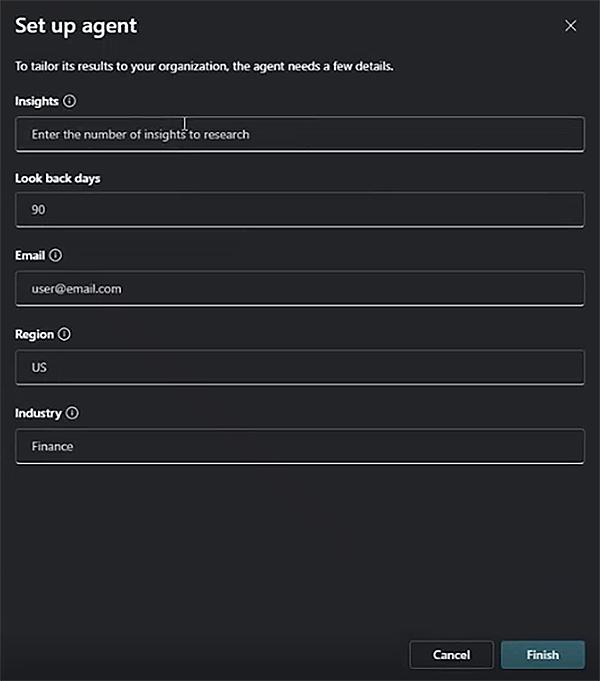
- Parameters - Specify parameters to customize the output, such as:
- Number of insights to research.
- Look-back period for threats.
- Email address for report delivery.
- Geographical region and industry scope.
- Run - After setup, access the agent overview page to run the agent manually or schedule it to run automatically.
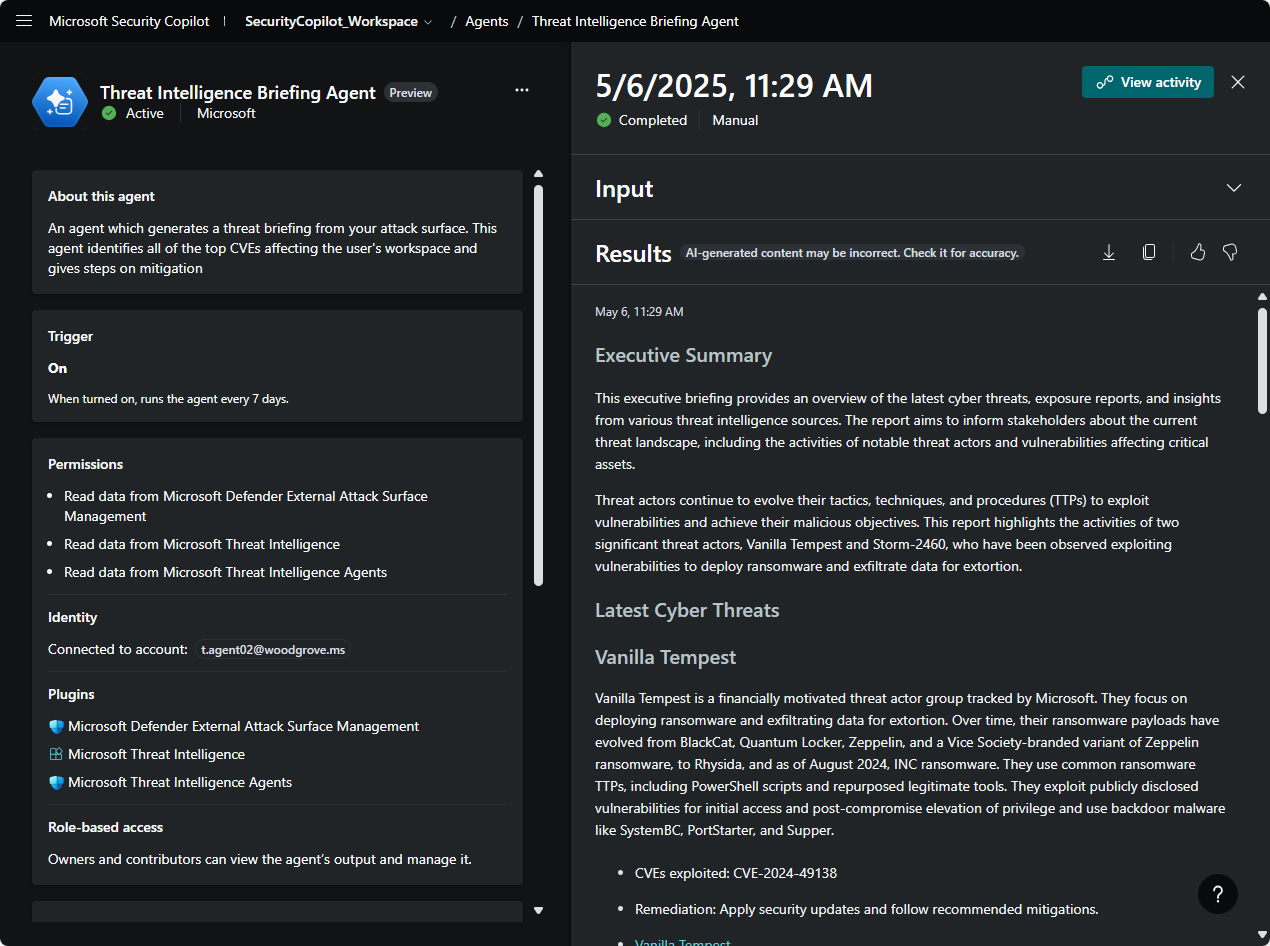
Generate and review threat intelligence reports
Once the agent runs, the generated reports appear under Activity in the Threat Intelligence Briefing Agent page. Each report includes:
- A summary of relevant threat information.
- Detailed technical analysis of actively exploited vulnerabilities.
- Potential organizational impacts.
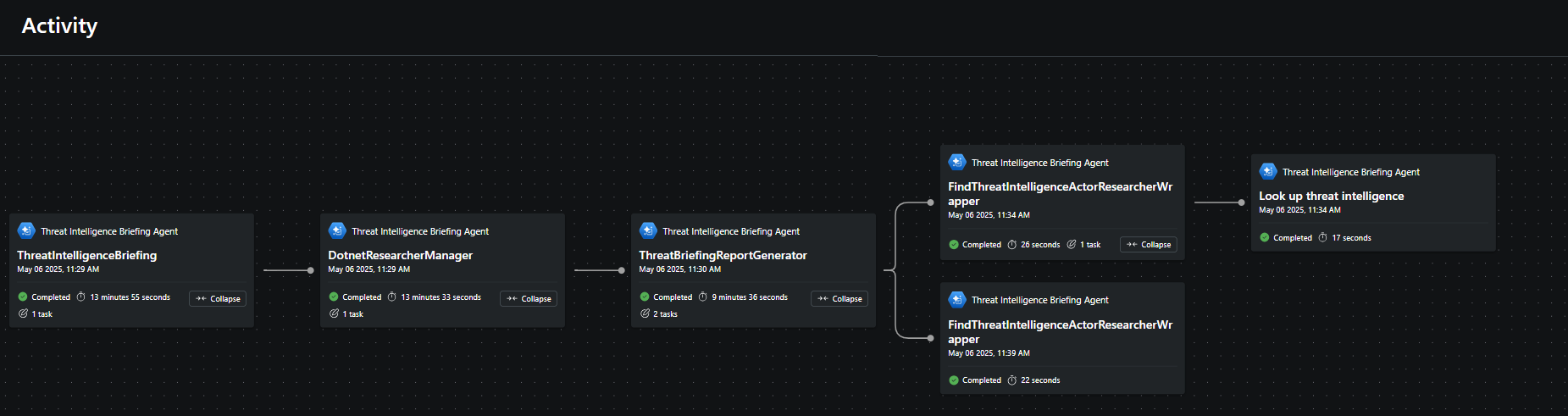
Select a report to assess its content and view the agent’s progress by clicking View activity.
Feedback
Feedback helps improve the agent’s performance and relevance. To provide feedback:
- Select the thumbs up or thumbs down button on the report.
- Add comments in the text box that appears.
- Select Submit to finalize your feedback.
Feedback ensures the agent continues to deliver high-quality, actionable insights tailored to your organization’s needs.