Protect your personally identifiable information
Some cyber threats try to get you to reveal personally identifiable information (PII), or any information that directly identifies you as an individual, in order to gain access to authorized services or steal privileged information.
Examples of PII include:
- Full names
- Addresses
- Email addresses
- Telephone numbers
- Social security numbers
- Birthdays
- Account information (such as usernames and passwords)
- Demographic information that identifies a person
- Educational records
Know the threat: Phishing
Phishing occurs when a cybercriminal pretends to be a trusted institution (like an HR department) or an individual (like your principal or a parent) to persuade you to share personal information. Phishing attempts are often sent through email or text messages, but sometimes appear as browser pop-ups or spoofed websites. In 2022, Microsoft Security blocked over 710 million phishing messages every week. Although robust security tools prevent many phishing attempts from ever reaching educators, messages still arrive in inboxes because social engineers are adept at their craft.
Identify phishing scams
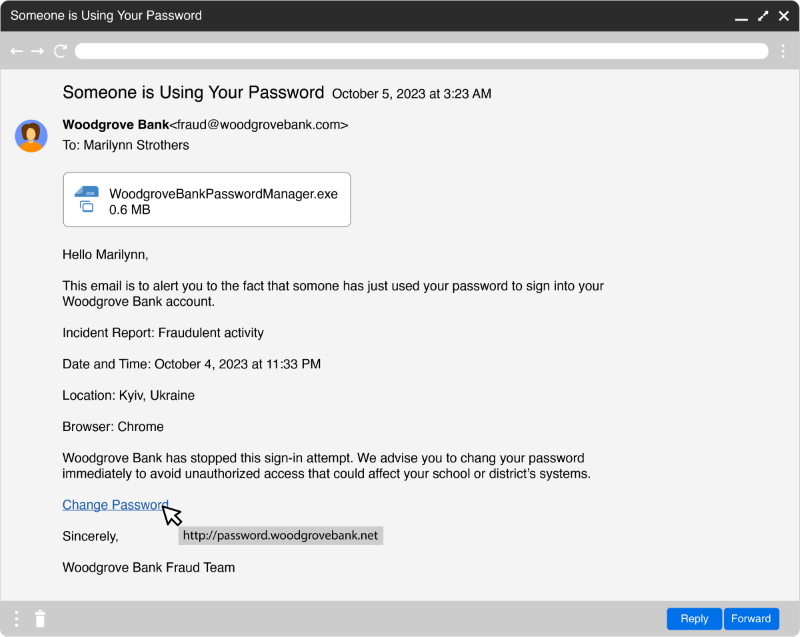
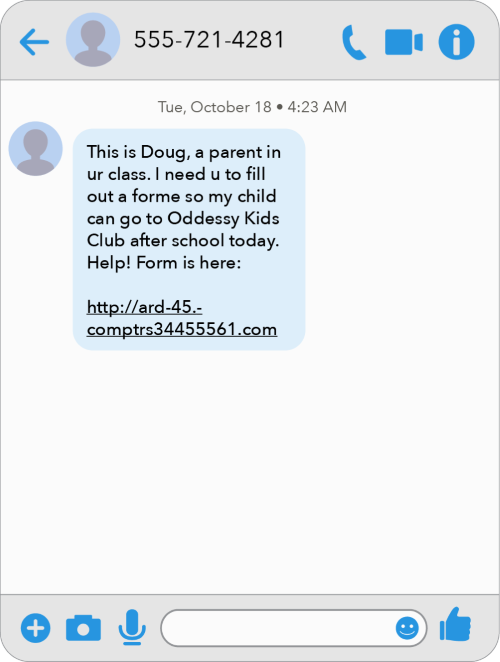
If you're the target of a phishing scam, would you know what to look for? Try to identify the red flags in the screenshots of a phishing email and a text message.
What can you do to protect PII?
It’s often more impactful to infiltrate an educator or administrator account, rather than a student account, because these credentials open large databases like Student Information Systems (SIS) that contain loads of student educational records. Your PII is also at risk of disclosure when phishing attempts are successful. Use these two strategies to help you protect PII.
Analyze messages with the AEIOU-Y strategy
When you slow down and reflect on the messages you receive, you can better identify phishing attempts. The AEIOU-Y strategy helps you decide whether something is real or fake. It stands for:
- Attachments: Does the email entice you to open or download an unsolicited attachment?
- Errors: Does the message include misspelled words, poor grammar, or incomplete sentences?
- Internet links: Does the email ask you to select a link that points to an unknown website? All websites that involve transactions or any exchange of private information must use https://. If the first part of the web address (http://) doesn’t include an s, never enter or submit PII.
- Origin: Does the sender’s email address contain extra letters, numbers, or words that are different from known addresses?
- Urgent: Does the message require you to act immediately to change your account, collect a reward, share information, or avoid cancellation?
- Yesterday: Was the message sent at an odd or unexpected time? Just like the letter Y is sometimes a vowel, the time that a message was sent can be a red flag or not.
When you apply the AEIOU-Y strategy to the email in the screenshot, you notice:
- Attachments: The message attachment looks like a useful application for managing passwords given the topic of fraudulent account activity. However, a company wouldn’t ask you to download and install a program when a simple password change would suffice.
- Errors: The body contains misspelled words like somone. The final paragraph also includes the word chang. A trusted organization wouldn’t send a message with obvious errors like this.
- Internet links: You can hover over a link and see the web address without selecting the link. This link points to a website that doesn’t use https:// which is a requirement for actions like password changes.
- Origin: Look for email addresses with small modifications or ones that appear out of the ordinary.
- Urgent: The message appears urgent. Although not all urgent messages are phishy, consider all of the other red flags before deciding to respond, select a link, or open an attachment. Remember: Social engineers prey upon people's natural instincts to immediately address a problem.
- Yesterday: The time the message was sent can be a red flag. Although it’s plausible that a company might send off-hours messages a phishing message that appears to be from a trusted individual like a principal or colleague won’t often be sent late at night.
Report phishing messages
Microsoft Outlook includes a built-in reporting tool that allows you to submit and remove phishing messages that might appear in your inbox. Doing so ensures that similar phishing attempts are blocked before they appear in other people's inboxes. When you consistently report known phishing exploits, your school's overall security improves.
Next steps
- Apply the AEIOU-Y strategy to any suspicious email or text messages you receive. Use the text presented earlier to practice.
- Review the steps for reporting phishing messages in Microsoft Outlook so that you can report any suspected phishing attempts in your inbox.