Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Explore how to integrate Microsoft Defender External Attack Surface Management (MDEASM) with Microsoft Security Exposure Management (MSEM) to enhance visibility and control over your organization's external exposures. By connecting MDEASM insights to MSEM using the External Attack Surface Management initiative, you can assess the risk associated with your organization's or vendor's external attack surface and manage your security posture more effectively within the Exposure Management portal.
There are two ways to use this initiative:
- Pre-built footprint: Provides high-level insights using a predefined set of external assets, without requiring a full MDEASM subscription.
- Full integration with MDEASM: Connects directly to your MDEASM subscription for comprehensive exposure analysis and asset-level details.
Using the EASM initiative with pre-built footprint
This approach with the initiative provides high-level insights without a full connection to the MDEASM subscription and supports pre-built footprints only and doesn't require an active MDEASM subscription.
Prerequisites: To configure your External Attack Surface initiative, you need to have Global Administrator role, or Core security settings (manage) permissions.
Go to the Initiatives page, select the External Attack Surface Protection, then choose Open initiative page.
Go to the Connect data source to open the settings tab.
Note
If you previously configured the initiative, you can select Switch data source to reconfigure it with new data.
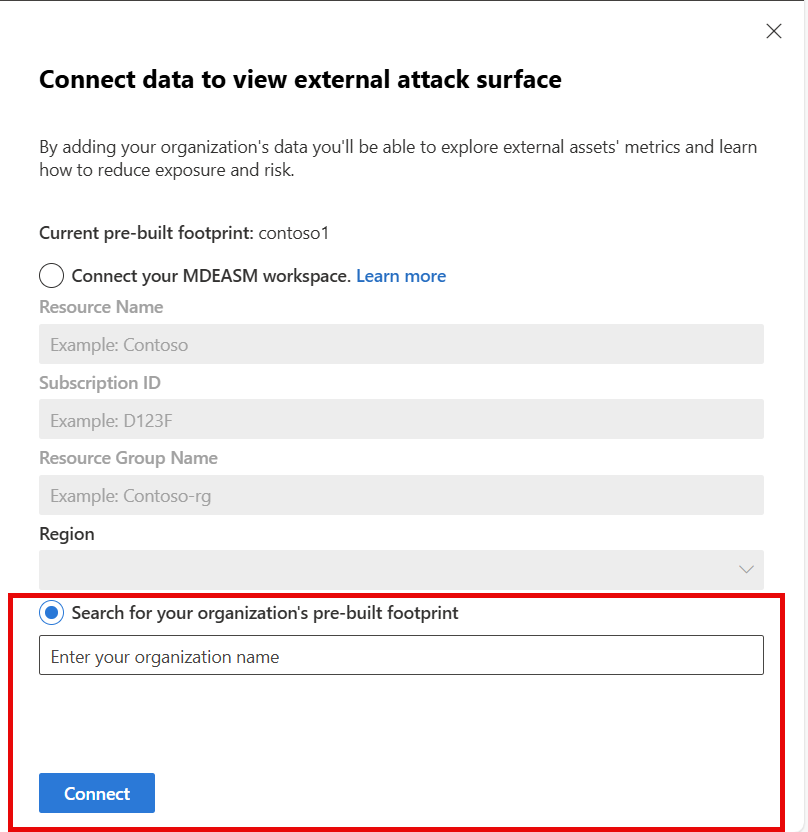
Choose Search for your organization's pre-built footprint.
Select the footprint you want to use from the list of available pre-built footprints and choose Connect.
In up to 1 hour, the initiative is populated with high-level metrics and scores from the selected footprint.
Note
This approach doesn't provide asset level information and detailed exposure information.
Using the EASM initiative with full MDEASM integration
Prerequisites: This approach requires a full MDEASM subscription (trial or paid) and provides comprehensive exposure analysis and asset-level details. To configure your External Attack Surface initiative, you need to have Global Administrator role, or Core security settings (manage) permissions.
Note
External attack surface assets do not support scoping, so all users with access can see all collected data.
Environment setup:
To deploy an MDEASM resource, follow these steps:
- Log into https://portal.azure.com.
- Create a Resource Group with the appropriate subscription and region.
- Deploy an MDEASM Resource within that group, see, Create a Defender EASM Azure resource. Each new resource will automatically get a free 30 day trial.
Discover the attack surface
You can discover your attack surface in two ways:
- Use the Get Started option to search for your organization and build a preconfigured attack surface.
- Or, create a custom discovery group by providing:
- Domains
- IP Blocks or Addresses (use example IPs such as 203.0.113.0 if needed)
- Hosts
- ASNs
- Emails
- WHOIS organization data
For more information, see Discovering your attack surface
Tip
The easiest path is to provide a host, domain, and any known external IP addresses.
Configure the initiative
Go to the Initiatives page, select the External Attack Surface Protection, then choose Open initiative page.
Go to the Connect data source to open the settings tab.
Note
If you previously configured the initiative, you can select Switch data source to reconfigure it with new data.
Choose Connect your MDEASM workspace.
To enable the initiative to pull data from your Defender EASM resource, enter the values from your resource's Essentials section on the Overview pane found in Azure.
- Resource Name
- Subscription ID
- Resource Group Name
- Region
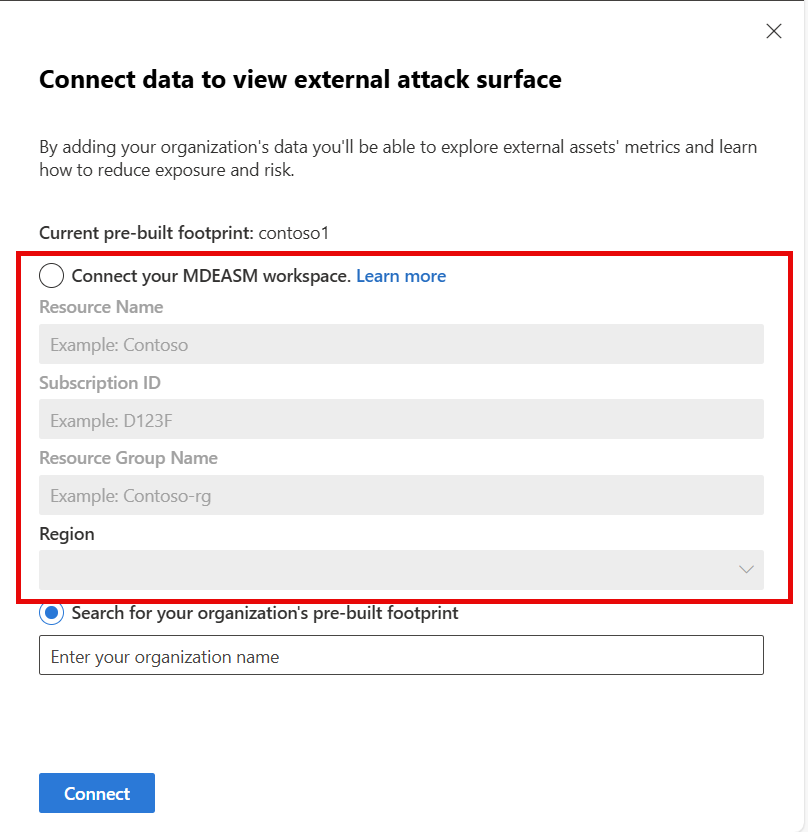
Select Connect. After validation, data will begin flowing into the graph, and metrics will calculate within 32 hours.
You can review your security initiative data through security metrics that reflect various exposure types as assessed by the External Attack Surface assessment engine. Select a metric to view additional information such as the exposed assets and their types.
Also explore the data integrated from EASM using the attack surface map to uncover insights related to your attack surface. You can search for various assets such as IP addresses, domains, hosts, and more, and review the findings on these assets.