Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article provides a general overview of Microsoft Purview Data Loss Prevention (DLP) policies for Fabric and Power BI. The target audience is Fabric administrators, security and compliance teams, and Fabric data owners. If you're a data owner and want to know how to respond when a policy tip tells you your item has a DLP policy match, see Respond to a DLP policy match in Fabric. If you're a Fabric admin or a security and compliance admin and need to audit alerts on DLP policy matches, see Monitor DLP policy matches in Fabric.
Overview
To help organizations detect and protect their sensitive data, Fabric supports Microsoft Purview Data Loss Prevention (DLP) polices. When a DLP policy for Fabric detects a supported item type containing sensitive information, the policy triggers the configured actions. These actions can include:
- Attaching a policy tip to the item that explains the nature of the sensitive content.
- Registering an alert for administrators on the data loss prevention Alerts page in the Microsoft Purview portal.
- Sending email alerts to administrators and specified users.
- Restricting access to the item.
For more detail, see How do DLP policies for Fabric and Power BI work.
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Licensing and permissions
Licensing
For information on licensing, see
Permissions
You can view data from DLP for Fabric and Power BI in Activity explorer. Four roles grant permission to Activity explorer; the account you use for accessing the data must be a member of any one of them.
To view the Activity explorer, your account must be a member of any of the following roles or higher.
- Compliance administrator
- Security administrator
- Compliance data administrator
Important
Microsoft recommends that you use roles with the fewest permissions. This recommendation helps improve security for your organization. Global Administrator is a highly privileged role that you should only use in scenarios where a lesser privileged role can't be used.
Billing
DLP evaluation workloads impact capacity consumption. For information about how this consumption is metered and billed, see Learn about Microsoft Purview billing models.
How DLP policies for Fabric and Power BI work
You define a DLP policy in the data loss prevention section of the Microsoft Purview portal. In the policy, you specify the conditions, such as which sensitivity labels and sensitive info types you want to detect. You also specify the actions that the system takes when it detects a policy match.
When DLP policies evaluate a supported item type, they check if it matches the conditions in a DLP policy. If it does, the policy's specified actions take place. DLP policies start with the following actions:
Semantic models:
DLP policies evaluate a semantic model whenever one of the following events occurs:
- Publish
- Republish
- On-demand refresh
- Scheduled refresh
Note
DLP evaluation of the semantic model doesn't occur if either of the following is true:
- An account using service principal authentication initiates the event (publish, republish, on-demand refresh, scheduled refresh).
- The semantic model owner is a service principal.
Fabric Items:
DLP policies evaluate a Fabric item, such as a lakehouse, SQL database, or Mirrored database, when the data within it changes. Changes include getting new data, connecting a new source, adding tables, updating existing tables, and more.
What happens when a Fabric DLP policy flags an item
When a DLP policy detects an issue with an item, it takes the following actions:
If you enable user notification in the policy, Fabric marks the item with an icon that indicates a DLP policy detected an issue with the item. When you hover over the icon, a hover card appears that provides an option to see the full details in a side panel. For more information about what you see in the side panel, see Respond to a DLP violation in Fabric.
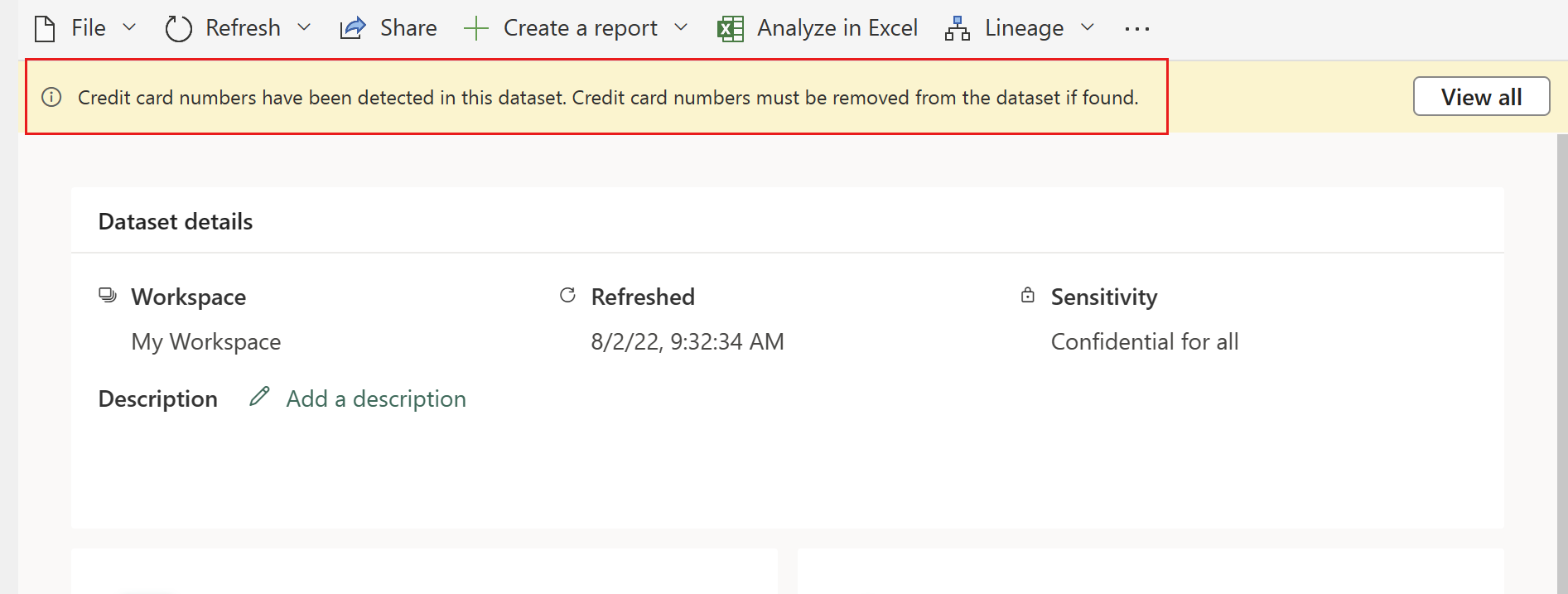
For semantic models, opening the details page shows a policy tip that explains the policy violation and how to handle the type of sensitive information detected. Selecting View all opens a side panel with all the policy details.
Note
If you hide the policy tip, it doesn't get deleted. It appears the next time you visit the page.
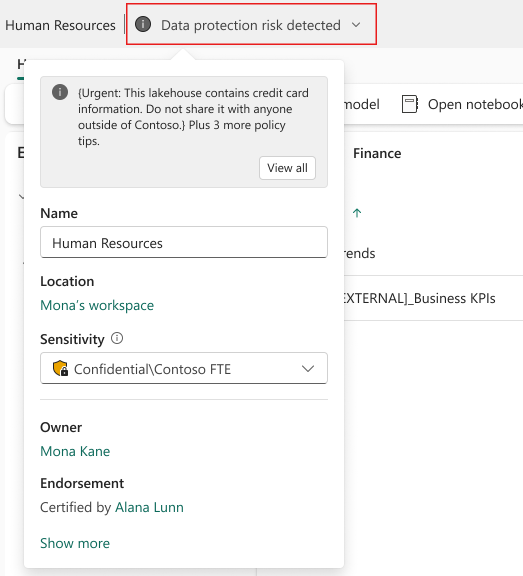
For lakehouses, the indication appears in the header in edit mode. Opening the flyout makes it possible to see more details about the policy tips affecting the lakehouse. Selecting View all opens a side panel with all the policy details.
If you enable alerts in the policy, an alert records on the data loss prevention Alerts page in the Microsoft Purview portal. If configured, an email sends to administrators and/or specified users. For more information, see Monitor and manage DLP policy violations.
Supported actions
When DLP policies evaluate a semantic model or lakehouse and find it matches the conditions in the policy, the policy's actions take effect. DLP policies for Fabric and Power BI support three actions:
- User notification through policy tips.
- Alerts. Administrators and users can receive alert emails. Additionally, administrators can monitor and manage alerts on the Alerts tab in the Purview portal.
- Restrict access. When you configure a policy with the restrict access action and a policy match occurs, the policy restricts access to the data owners or to members of the organization, depending on the policy configuration. All other users lose access to the item.
For information about what triggers DLP evaluation, see How DLP policies for Fabric and Power BI work.
Supported item types
DLP policies for Fabric and Power BI currently support (preview) the following item types.
- Semantic models
- Lakehouses
- KQL databases
- Mirrored databases
- SQL databases
See Considerations and limitations for exceptions.
Supported condition types
DLP policy rules for Fabric and Power BI support sensitivity labels and a subset of sensitive info types (see considerations and limitations) as conditions.
Configure a DLP policy for Fabric and Power BI
For information about creating a DLP policy for Fabric or Power BI, see Help prevent sharing Power BI reports with credit card numbersand adapt it to your own scenario.
Considerations and limitations
- DLP policies apply to workspaces. Only workspaces hosted in Fabric or Premium capacities are supported. For more information, see Microsoft Fabric concepts and licenses.
- DLP policy templates aren't supported for Fabric DLP policies. When creating a DLP policy for Fabric, choose the custom policy option.
- DLP policies for Fabric aren't supported for sample semantic models, streaming datasets, or semantic models that connect to their data source via DirectQuery or live connection. This limitation includes semantic models with mixed storage, where some of the data comes via import-mode and some comes via DirectQuery.
- DLP policies for Fabric apply only on data in Lakehouse Tables/ folder stored in Delta format.
- DLP policies for Fabric support all the primitive Delta types except timestamp_ntz.
- DLP policies for Fabric aren't supported for the following Delta Parquet data types:
- Binary, timestamp_ntz, Struct, Array, List, Map, Json, Enum, Interval, Void.
- Data with LZ4, Zstd, and Gzip compression codecs.
- Exact data match (EDM) classifiers and trainable classifiers aren't supported by DLP for Fabric. If you select an EDM or trainable classifier in the condition of a policy, the policy returns no results even if the semantic model or lakehouse contains data that satisfies the EDM or trainable classifier. Other classifiers specified in the policy return results, if any.
- DLP policies for Fabric aren't supported in the China North region. See How to find the default region for your organization to learn how to find your organization's default data region.
- Azure capacities aren't supported for DLP in Fabric in the following clusters:
- WUS3
- WUS2
- SCUS
- Onboarding a new tenant to DLP can take a few hours, depending on the number of supported workspaces that are being onboarded.