Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
It's important to secure the sensitive data in your cloud flows to prevent unauthorized access and ensure compliance with data protection standards. This article provides best practices for securing data in your Power Automate flows.
Avoid hardcoding sensitive information
To avoid exposing sensitive data in your cloud flows, follow these best practices:
Avoid embedding sensitive information, such as passwords or API keys, directly in your flow. Power Automate lets users view flow run history and dive into a trigger or action's inputs and outputs. Hardcoding these details can expose them to anyone with access to the flow, increasing the risk of data breaches.
Use environment variables to store sensitive information instead of hardcoding it. You can manage and update the value of environment variables centrally and without modifying the flow itself. Learn more in Use environment variables for Azure Key Vault secrets.
Use Azure Key Vault
Azure Key Vault is a cloud service for securely storing and accessing secrets, keys, and certificates. It offers advantages over other methods of protecting sensitive information:
Azure Key Vault provides a centralized solution for managing sensitive information, ensuring that your data is encrypted and access is tightly controlled.
Power Automate can integrate with Azure Key Vault using the Azure Key Vault connector or environment variables. Using the connector or environment variables lets your flows retrieve secrets dynamically during execution without exposing them in the flow design.
Access to Azure Key Vault uses role-based access control through Microsoft Entra ID, ensuring that only authorized users and applications can access the stored secrets.
Use secure inputs and secure outputs
Another way to protect sensitive data in your flows is the secure inputs and secure outputs feature in Power Automate. It ensures that sensitive information isn't visible in the run history or audit logs and helps maintain the privacy and security of your data. Learn more in Manage sensitive input like passwords.
Turn on secure inputs and secure outputs (new designer)
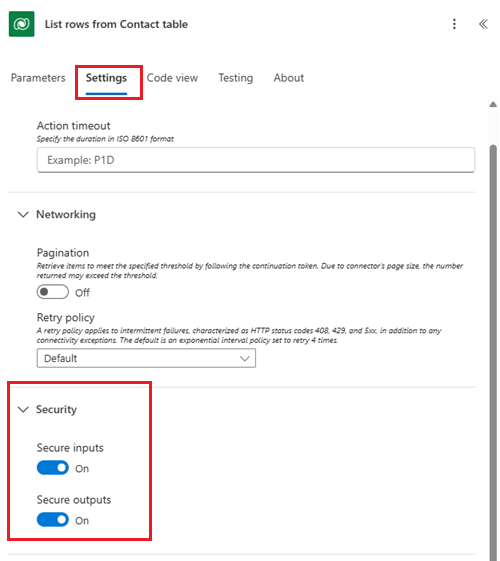
In the new designer, select an action, and then select the Settings tab.
Under Security, select the Secure inputs and Secure outputs toggles.
Turn on secure inputs and secure outputs (classic designer)
In the classic designer, select the ellipsis (…) on an action, and then select Settings.
Select the Secure Inputs and Secure Outputs toggles.
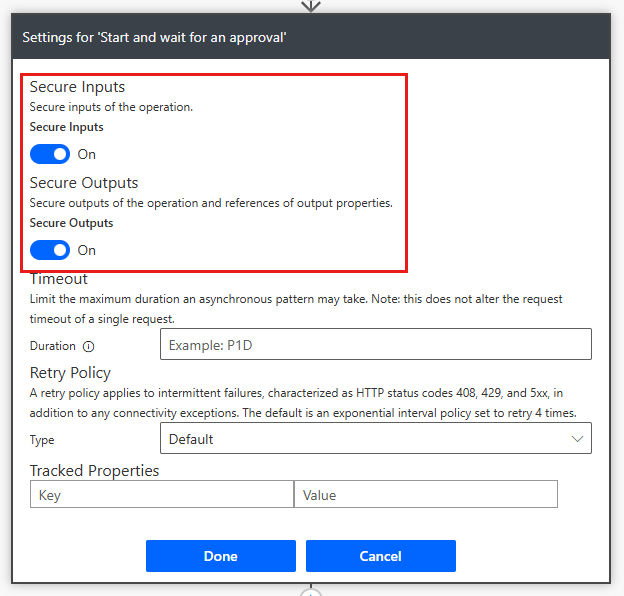
Select Done.
Secure the HTTP request trigger
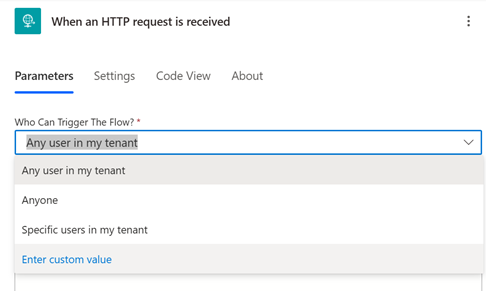
The When an HTTP request is received trigger lets you initiate a workflow by sending an HTTP request to the endpoint generated by the flow. To ensure that only authorized users can trigger the workflow, implement the following security measures:
Use a Microsoft Entra ID token: Configure your flow to require a Microsoft Entra ID token for authentication. Configure the token to restrict access to any user in the tenant or to specific users or principals in the tenant. Learn more in Add OAuth authentication for HTTP request triggers.
Use IP pinning: Environment admins can configure a set or range of IP addresses that are permitted to interact with Power Platform resources. Setting up an IP firewall ensures that only requests from allowed IP addresses can trigger the workflow. Learn more in IP firewall in Power Platform environments.