Applies to: ✅ Warehouse in Microsoft Fabric
Auditing in Fabric Data Warehouse provides enhanced security and compliance capabilities by tracking and recording database events.
You can configure SQL audit logs in the Fabric portal or via REST API. The SQL audit logs feature is currently in preview.
Prerequisites
- A Fabric workspace with an active capacity or trial capacity.
- You should have access to a Warehouse item within a workspace.
- You must have the Audit permission to configure and query audit logs. For more information, see Permissions.
You can configure SQL audit logs using the Fabric portal or via REST API.
In your Fabric workspace, select the Settings of your warehouse item.
Select the SQL audit logs page.
Enable the setting Save events to SQL audit logs.
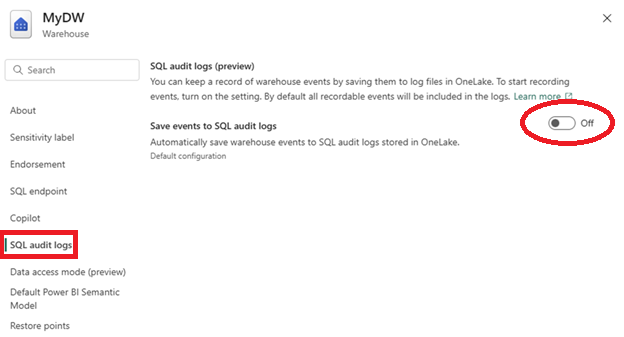
By default, all actions are enabled and retained for nine years.
You can configure which events will be captured by SQL audit logs under Events to record. Select which event categories or individual audit action groups you want to capture. Only select the events your organization requires to optimize storage and relevance.
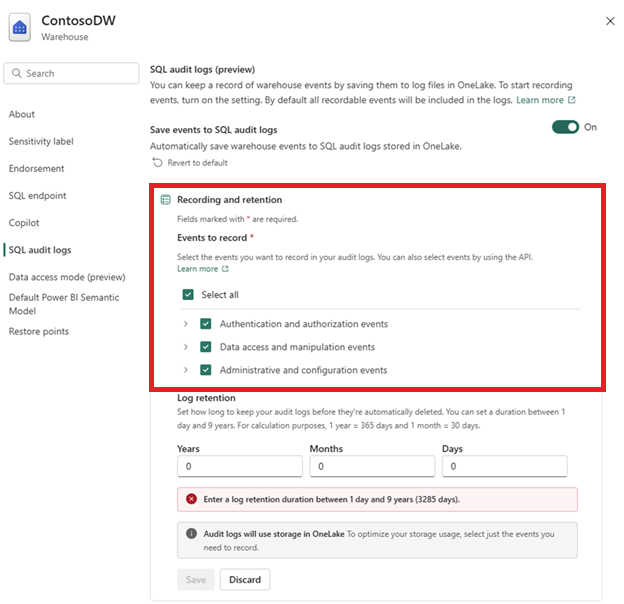
Specify a desired log retention period in Years, Months, and Days.
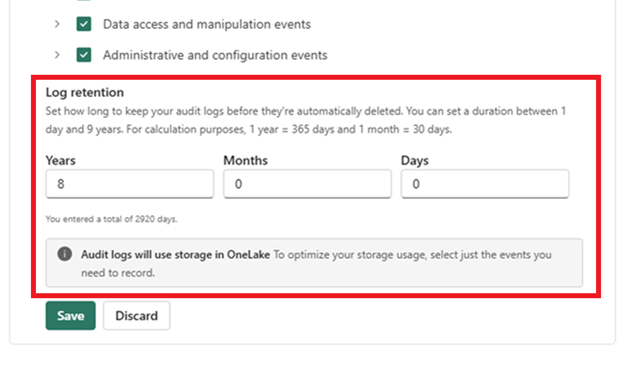
Select Save to apply your settings.
Your warehouse will now record the selected audit events and store the logs securely in OneLake.
Download and install Visual Studio Code.
Install the REST Client extension from the Visual Studio Marketplace.
Obtain the bearer token using the following steps. You can find your Power BI bearer token in your browser's developer tools or via PowerShell.
To use the Edge developer tools to find your Power BI bearer token:
- Open your Microsoft Fabric workspace in a browser (Microsoft Edge).
- Press F12 to open Developer Tools.
- Select the Console tab. If necessary, select Expand Quick View to reveal the console prompt
>.
- Type the command
powerBIAccessToken and press Enter. Right-click on the large unique string returned in the console and select Copy string contents.
- Paste it in place of
<bearer token> in the following scripts.
To use PowerShell to find your Power BI bearer token:
Install the MicrosoftPowerBIMgmt module from Microsoft Power BI Cmdlets for Windows PowerShell and PowerShell Core.
Install-Module -Name MicrosoftPowerBIMgmt
Use Connect-PowerBIServiceAccount to connect to Power BI PowerShell, and retrieve the bearer token.
Connect-PowerBIServiceAccount
$token = (Get-PowerBIAccessToken).Authorization
Write-Output "Bearer $token"
Once you have obtained the Power BI bearer token, you can send a PATCH request using the REST Client extension. In VS Code, create a new text file in VS Code with the .http extension.
Copy and paste the following request:
PATCH https://api.fabric.microsoft.com/v1/workspaces/<workspaceId>/warehouses/<warehouseId>/settings/sqlAudit
content-type: application/json
Authorization: Bearer <BEARER_TOKEN>
{
"state": "Enabled",
"retentionDays": "0"
}
- Replace
<workspaceId> and <warehouseId> with the corresponding Fabric workspace and warehouse IDs. To find these values, visit your warehouse in the Fabric portal.
<workspaceID>: Find the workspace GUID in the URL after the /groups/ section, or by running SELECT @@SERVERNAME in an existing warehouse. For example, 11aaa111-a11a-1111-1aaa-aa111111aaa. Don't include the / characters.<warehouseID>: Find the warehouse GUID in the URL after the /warehouses/ section, or by running SELECT @@SERVERNAME in an existing warehouse. For example, 11aaa111-a11a-1111-1aaa-aa111111aaa. Don't include the / characters.
- Replace
<BEARER_TOKEN> with your bearer token.
- Setting
state to "Enabled" activates auditing (use "Disabled" to turn it off).
- The
retentionDays parameter is set to 0 by default for unlimited retention.
Important
In the extension example code, you must include an empty line immediately after providing the bearer token. This empty line signals the extension where the HTTP headers end and the API command body begins, allowing it to correctly distinguish between the two.
Select Send Request.
Check audit log status with the REST API
To verify if the SQL Audit Logs are enabled, send a GET request using the same REST Client extension.
- In VS Code, create a new text file in VS Code with the
.http extension.
- Copy and paste the following request, providing your own
workspaceId, <warehouseId>, and <BEARER_TOKEN>.
GET https://api.fabric.microsoft.com/v1/workspaces/<workspaceId>/warehouses/<warehouseId>/settings/sqlAudit
content-type: application/json
Authorization: Bearer <BEARER_TOKEN>
The response returns ENABLED or DISABLED and the current configuration of auditActionsAndGroups.
SQL audit logs rely on predefined action groups that capture specific events within the database. For details on audit action groups, see SQL audit logs in Fabric Data Warehouse.
In VS Code, create a new text file in VS Code with the .http extension.
Copy and paste the following request, providing your own workspaceId, <warehouseId>, and <BEARER_TOKEN>.
POST https://api.fabric.microsoft.com/v1/workspaces/<workspaceId>/warehouses/<warehouseId>/settings/sqlAudit
content-type: application/json
Authorization: Bearer <BEARER_TOKEN>
[ "DATABASE_OBJECT_PERMISSION_CHANGE_GROUP" ]
Select Send Request.
Query audit logs
SQL audit log data is stored in .XEL files in the OneLake, and can only be accessed using the sys.fn_get_audit_file_v2 Transact-SQL (T-SQL) function. For more information on how audit files are stored in the OneLake, see SQL audit logs in Fabric Data Warehouse.
From the SQL query editor or any query tool such as SQL Server Management Studio (SSMS) or the mssql extension with Visual Studio Code, use the following sample T-SQL queries, providing your own workspaceId and <warehouseId>.
SELECT *
FROM sys.fn_get_audit_file_v2
('https://onelake.blob.fabric.microsoft.com/<workspaceId>/<warehouseId>/Audit/sqldbauditlogs/'
, default, default, default, default);
To filter logs by time range, use the following query:
SELECT *
FROM sys.fn_get_audit_file_v2
('https://onelake.blob.fabric.microsoft.com/<workspaceId>/<warehouseId>/Audit/sqldbauditlogs/'
, default, default, '2025-03-30T08:40:40Z', '2025-03-30T09:10:40Z');
Related content


