Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Overview
When Exchange Server is deployed in a hybrid configuration, features such as Free/Busy, MailTips, and Photos become available between Exchange Server and Exchange Online, providing a seamless experience for users. These features are automatically configured when you run the Hybrid Configuration Wizard (HCW) for the first time.
To enable hybrid feature use, Exchange Server utilizes a shared Service Principal with Exchange Online for secure communication. The HCW uploads the current Auth Certificate from your Exchange organization to the shared Service Principal to facilitate this process.
As announced in the Retirement of Exchange Web Services in Exchange Online blog post, Exchange Web Services (EWS) is set to be fully deprecated in Exchange Online in October 2026 for non-Microsoft (third-party) applications and services. In the Security Related Updates in Exchange Online blog post, we announced that we are also removing EWS dependencies from our own (first-party) apps and services, and this change is expected before October 2026.
Exchange Server, used in a hybrid configuration, is affected by this change as it uses the shared Service Principal from Exchange Online (first-party). To accommodate this change, Exchange Server replaces EWS API calls with REST-based Graph API calls in hybrid scenarios in near future. This design change involves multiple steps, with the first step being the use of a separate application in Microsoft Entra ID instead of the shared Service Principal.
This documentation outlines the steps required to create a dedicated Exchange application in Entra ID for Exchange hybrid configurations as part of the updated design. Exchange Server continues using EWS after the dedicated Exchange application is created and configured. The switch to REST-based Graph API as a replacement for EWS will be made with an update that is expected to be published in near future.
Important
If you've already configured the dedicated Exchange hybrid app or previously had a hybrid configuration, we strongly recommend running the script in Service Principal Clean-Up Mode. This mode removes any certificates that were uploaded to the first-party Service Principal's keyCredentials and not cleaned up. If you're unsure whether action is needed, simply run the script in Service Principal Clean-Up Mode to remove any leftover certificates.
To learn more about this change and its implications, we recommend reading the Exchange Server Security Changes for Hybrid Deployments blog post, which provides detailed context and guidance.
Prerequisites
Before configuring and using the dedicated Exchange hybrid application, you must first set up either Classic Full or Modern Full hybrid using the Hybrid Configuration Wizard.
The dedicated Exchange hybrid application feature is supported starting with the following Exchange Server builds:
| Version | Build Number |
|---|---|
| Exchange Server SE RTM | 15.2.2562.17 |
| Exchange Server 2019 CU15 with April 2025 HU | 15.2.1748.24 |
| Exchange Server 2019 CU14 with April 2025 HU | 15.2.1544.25 |
| Exchange Server 2016 CU23 with April 2025 HU | 15.1.2507.55 |
Important
The latest version of the Hybrid Configuration Wizard (HCW) supports configuring the dedicated Exchange Hybrid application. However, HCW does not enable the feature automatically. To activate it after configuration, follow the steps outlined in the How to enable the dedicated Exchange hybrid application feature via setting override section. Additionally, HCW does not automatically clean up certificates that may have been previously uploaded to the first-party service principal's keyCredentials. To perform this clean-up and mitigate CVE-2025-53786, run the script in Service Principal Clean-Up Mode. This ensures that any residual certificates embedded in the service principal are removed.
Microsoft provides a script to create the dedicated Exchange hybrid application in Entra ID and to configure the feature. There are two distinct scenarios in which the script can be executed, each with its own set of prerequisites. The modes are explained in the Configuration section of this documentation.
All-in-one Configuration Mode:
This mode is designed for simplicity and is suitable for most customers. It allows for a streamlined setup process, making it ideal for environments where ease of configuration is a priority.
Split Execution Configuration Mode:
This mode is intended for more advanced scenarios. It's useful if your Exchange server lacks outbound connectivity to the Graph API or Entra ID endpoints, or if the Exchange Server administrator doesn't have sufficient permissions to create and configure the application in Entra ID.
If you perform any of the steps on a non-Exchange Server, ensure that the computer is joined to the same forest where your Exchange organization resides.
Connectivity
The script utilizes the Microsoft Graph API to create and manage applications in Microsoft Entra ID. When running the script in All-in-one Configuration Mode, the system executing the script requires outbound connectivity to the specified endpoints. In Split Execution Configuration Mode, the system used to create or manage the application in Entra ID needs outbound access to these endpoints. You should choose the endpoint where your tenant resides, such as Global. For more information, see the National Microsoft Entra ID Endpoints and National Microsoft Graph Endpoints documentation.
To verify your server's ability to connect to the Graph and Entra ID endpoints, you can use the Test-NetConnection PowerShell cmdlet. This example demonstrates how to validate the connection to these endpoints using the Global endpoints:
Test-NetConnection -ComputerName login.microsoftonline.com -Port 443
Test-NetConnection -ComputerName graph.microsoft.com -Port 443
Permissions
The account used for creating the application in Microsoft Entra ID must possess the following permissions:
| Least privileged permissions | Higher privileged permissions |
|---|---|
Application Administrator |
Global Administrator |
For more details about the roles in Entra ID, see the Microsoft Entra built-in roles documentation.
The account used for configuring the Auth Server object and creating the Setting Override to enable the feature in Exchange Server must have the following permissions within the on-premises organization:
| Least privileged permissions | Higher privileged permissions |
|---|---|
View-Only Configuration andOrganization Client Access andOrganization Configuration |
Organization Management |
For detailed information about the various roles in Exchange Server, refer to the Organization Management documentation.
To configure the Auth Server and create the Setting Override, ensure that the script is executed on a server with the Mailbox role installed and a build that supports this feature.
To use the script for resetting the keyCredentials of the shared Service Principal, as detailed in the Service Principal Clean-Up Mode section, ensure that the account running the script has the following permissions:
| Least privileged permissions | Higher privileged permissions |
|---|---|
N/A |
Global Administrator |
Auth Certificate
The Auth Certificate is a key component in Microsoft Exchange Server, supporting various security and authentication scenarios. Proper management of the Auth Certificate is essential for maintaining the security and reliability of Exchange Server operations.
In the dedicated Exchange hybrid application use case, it facilitates JSON Web Token (JWT) assertion-based authentication for server-to-server (S2S) communication. This allows an Exchange Server to authenticate by presenting a signed JWT instead of relying on a password or interactive login. The JWT, issued and signed by a trusted authority, contains claims that verify the Exchange Server's identity and permissions, enabling secure, token-based access to resources.
Tip
You can use the MonitorExchangeAuthCertificate script to validate your OAuth certificate. If you need to update your OAuth certificate, follow the steps in the Maintain the Exchange Server OAuth certificate documentation.
In some scenarios described in this documentation, you need to export the Auth Certificate. Make sure not to export the private key of the certificate. To export the public key of the certificate, you can use the following PowerShell script.
In this example, the certificate is exported to C:\AuthCertExport. If you wish to export the certificate to a different location, modify the $exportFilePath variable to your desired path. Ensure you run the script from an elevated Exchange Management Shell (EMS):
# Change the path if you want to export the certificates to a different location
$exportFilePath = "C:\AuthCertExport"
$authConfig = Get-AuthConfig
New-Item -Type Directory -Path C:\AuthCertExport -Force | Out-Null
if (-not([System.String]::IsNullOrEmpty($authConfig.CurrentCertificateThumbprint))) {
$thumbprint = $authConfig.CurrentCertificateThumbprint
Write-Host "[+] Auth Certificate thumbprint: $thumbprint"
try {
$currentAuthCertificate = Get-ChildItem -Path Cert:\LocalMachine\My\$thumbprint
Export-Certificate -Cert $currentAuthCertificate -FilePath "$exportFilePath\$thumbprint.cer" -Type CERT | Out-Null
Write-Host "[+] Certificate was successfully exported to: $exportFilePath"
} catch {
Write-Host "[+] We hit the following exception: $_" -ForegroundColor Red
}
}
if (-not([System.String]::IsNullOrEmpty($authConfig.NextCertificateThumbprint))) {
$thumbprint = $authConfig.NextCertificateThumbprint
Write-Host "[+] Next Auth Certificate thumbprint: $thumbprint"
try {
$currentAuthCertificate = Get-ChildItem -Path Cert:\LocalMachine\My\$thumbprint
Export-Certificate -Cert $currentAuthCertificate -FilePath "$exportFilePath\$thumbprint.cer" -Type CERT | Out-Null
Write-Host "[+] Certificate was successfully exported to: $exportFilePath"
} catch {
Write-Host "[+] We hit the following exception: $_" -ForegroundColor Red
}
}
Changes made by the script
The ConfigureExchangeHybridApplication.ps1 script performs various operations based on the selected option. These operations include configuring and enabling the dedicated Exchange hybrid application feature, or deleting or modifying the existing Exchange Online Service Principal. This section outlines the specific operations executed by the script.
CreateApplication
- Create a new application with name
ExchangeServerApp-{Guid of the organization}in Entra ID - Assign the user who was used to run the script as an owner of the application in Entra ID
- Assign the
full_access_as_appEWS API permissions (to be replaced with Graph API permission in near future) - Grant tenant-wide admin consent
- This change needs to be confirmed during the runtime of the script
- The script doesn't enable the feature via Setting Override if tenant-wide admin consent hasn't been granted
UpdateCertificate
- Upload the current Auth Certificate to the application in Entra ID
- Upload the new next Auth Certificate (if it exists) to the application in Entra ID
- Delete any certificate from the application, which has expired
ConfigureAuthServer
- Update the
EvoSTSorEvoSTS - {Guid}Auth Server object- Set the
ApplicationIdentifierto theappIdof the application in Entra ID - Add the SMTP Remote Routing Domain to the
DomainNameproperty
- Set the
ConfigureTargetSharingEpr
- Identify any enabled
OrganizationRelationshipconfigured between Exchange Server and Exchange Online - Use AutoDiscover to query the
Exchange Web Services (EWS)endpoint - Set the
TargetSharingEprto the EWS endpoint returned by AutoDiscover
EnableExchangeHybridApplicationOverride
- If the script runs in All-in-one Configuration Mode
- Validate if the application in Entra ID has the correct API permissions and tenant-wide admin consent granted
- Create a new Setting Override to enable the feature on-premises by using the following parameters / values:
- Name:
EnableExchangeHybrid3PAppFeature - Component:
Global - Section:
ExchangeOnpremAsThirdPartyAppId - Parameters:
Enabled=true - Reason:
"Created by {Name of the Script} on {timestamp}"
- Name:
DeleteApplication
- Delete the dedicated Exchange application in Entra ID
ResetFirstPartyServicePrincipalKeyCredentials
- Remove all existing
keyCredentialsfrom theOffice 365 Exchange Onlinefirst-party application Service Principal - If a thumbprint was provided via
CertificateInformationparameter, purge only the certificate that matches the thumbprint and all certificates, which are already expired
Configuration using the script
Microsoft provides the ConfigureExchangeHybridApplication.ps1 script to configure the dedicated Exchange hybrid application feature. This section explains the most common scenarios covered by the script. Detailed documentation for the script and its parameters can be found in the ConfigureExchangeHybridApplication.ps1 script documentation.
If your on-premises organization has hybrid relationships with multiple tenants (1:N), you need to run the script multiple times. Each time, use an account from the tenant you want to configure the dedicated Exchange hybrid application feature for. Doing so ensures that the script creates and configures the application in each of your tenants.
Depending on the size of your organization, it may take up to 60 minutes for the dedicated Exchange hybrid application configuration to be recognized by the responsible Exchange Server processes. During this time, you might notice that features such as Free/Busy, MailTips, and Photos are temporarily unavailable.
All-in-one Configuration Mode
For most customers, the All-in-one Configuration Mode is the recommended way to configure this feature. To use this mode, run the script on a Mailbox server with outbound connectivity, as described in the Connectivity section. The server must be running an Exchange Server build that supports the dedicated Exchange hybrid application feature. Additionally, ensure you have the required permissions.
Important
The All-in-one Configuration Mode isn't compatible with Windows Server Core. If you're using Windows Server Core, follow the instructions in the Split Execution Configuration Mode section.
.\ConfigureExchangeHybridApplication.ps1 -FullyConfigureExchangeHybridApplication
By default, the script runs against the Microsoft 365 Worldwide cloud. If your Microsoft 365 tenant is in a different cloud, use the AzureEnvironment parameter. In the following example, the application is created in the Microsoft 365 operated by 21Vianet cloud:
.\ConfigureExchangeHybridApplication.ps1 -FullyConfigureExchangeHybridApplication -AzureEnvironment "ChinaCloud"
Split Execution Configuration Mode
If your Mailbox server, for example, doesn't have outbound Connectivity to Microsoft Graph or Entra ID, you can run the script in multiple steps. Some of these steps don't need to be performed on an Exchange server.
First, export the Auth Certificate (and, if available, the next Auth Certificate) with its public key. Use the script provided in the Auth Certificate section to perform the export. Don't export the private key of the certificate.
Next, copy the exported certificates to a machine with outbound connectivity, as described in the Connectivity section. On that machine, run the script to create the application in Entra ID. The script displays your Tenant ID and the appId of the newly created application. Be sure to make a note of both values, as you need them in a later step:
.\ConfigureExchangeHybridApplication.ps1 -CreateApplication -UpdateCertificate -CertificateMethod "File" -CertificateInformation "C:\Certificates\CurrentAuthCertificate.cer"
If multiple Auth Certificates were exported in the previous step, you must run the script twice. The CreateApplication step isn't required for the second run:
.\ConfigureExchangeHybridApplication.ps1 -UpdateCertificate -CertificateMethod "File" -CertificateInformation "C:\Certificates\NewNextAuthCertificate.cer"
This step must be performed on a Mailbox server. During this process, the Auth Server is configured, existing organization relationships between Exchange Server and Exchange Online are updated, and the dedicated Exchange hybrid application feature is enabled. You need to provide the ID of your tenant, the appId of the newly created application in Entra ID, and the remote routing domain:
.\ConfigureExchangeHybridApplication.ps1 -ConfigureAuthServer -ConfigureTargetSharingEpr -EnableExchangeHybridApplicationOverride -CustomAppId "<appId>" -TenantId "<tenantId>" -RemoteRoutingDomain "<organization>.mail.onmicrosoft.com"
Update Certificate Mode
The steps in this section aren't required when configuring and enabling the dedicated Exchange hybrid application feature for the first time. The steps can be used to update the certificate if the Auth Certificate expired or was replaced. For more information about maintaining the Auth Certificate, see the Maintain the Exchange Server OAuth certificate documentation.
If your Mailbox server has outbound connectivity, as described in the Connectivity section, run the script as follows:
.\ConfigureExchangeHybridApplication.ps1 -UpdateCertificate
If your Mailbox server doesn't have outbound connectivity to Microsoft Graph and Entra ID, follow the instructions in the Split Execution Configuration Mode section to export the new Auth Certificate. Copy the certificate to a machine with outbound connectivity (which doesn't have to be an Exchange server), as described in the Connectivity section. Then, run the script as follows:
.\ConfigureExchangeHybridApplication.ps1 -UpdateCertificate -CertificateMethod "File" -CertificateInformation "C:\Certificates\NewAuthCertificate.cer"
Delete Application Mode
This step isn't required when configuring and enabling the dedicated Exchange hybrid application feature. However, if needed, you can use the following command to delete the application created in Entra ID. This command can be executed on a non-Exchange server.
Deleting the application via the ConfigureExchangeHybridApplication.ps1 script doesn't revert the Exchange hybrid application configuration in your environment. If you need to switch back, follow the steps in the How to roll back from dedicated Exchange hybrid application section of this documentation.
To delete the application in Entra ID (you'd do this action only when rolling back the change or troubleshooting the creation of a new application in Entra ID), run the script as follows:
.\ConfigureExchangeHybridApplication.ps1 -DeleteApplication
Service Principal Clean-Up Mode
As part of the previous Exchange hybrid design, the Hybrid Configuration Wizard (HCW) uploaded the current Auth Certificate from your Exchange organization to the first-party Service Principal. This practice is no longer recommended and should not be performed. The Auth Certificate must now be uploaded exclusively to the dedicated Exchange hybrid application.
After enabling the dedicated Exchange hybrid application feature and ensuring all your Exchange servers are running an Exchange build that supports this feature, it's strongly recommended to clean up the certificates that were previously uploaded to the first-party Service Principal. The commands outlined in this section can be executed on any computer with outbound internet connectivity.
Purging the keyCredentials of the first-party Service Principal while any Exchange servers are still running builds older than those listed in the Exchange build that supports this feature section breaks rich coexistence hybrid features for those servers.
Warning
If you run the HCW after configuring the dedicated Exchange hybrid application feature and select the Oauth, Intra Organization Connector and Organization Relationship configuration option, the Auth Certificate will be uploaded to the first-party Service Principal again. It's strongly recommended to repeat the steps to purge the Auth Certificate from the first-party Service Principal in this case.
To purge all keyCredentials of the first-party Service Principal, run the script as follows:
.\ConfigureExchangeHybridApplication.ps1 -ResetFirstPartyServicePrincipalKeyCredentials
To purge a specific certificate and all expired certificates from the keyCredentials, run the script as follows and provide the thumbprint of the certificate to be deleted:
.\ConfigureExchangeHybridApplication.ps1 -ResetFirstPartyServicePrincipalKeyCredentials -CertificateInformation "1234567890ABCDEF1234567890ABCDEF12345678"
Validate OAuth Connectivity Status
To verify that OAuth authentication is functioning correctly between Exchange Server and Exchange Online, use the Test-OAuthConnectivity cmdlet:
Test-OAuthConnectivity -Service EWS -TargetUri https://outlook.office365.com -Mailbox "<OnPremisesMailboxSmtpAddress>" | Format-List
If the ResultType is Success and the Detail section includes the appId of your dedicated Exchange hybrid application, it indicates that Exchange Server successfully acquired an OAuth token. The OAuth request is initiated by the server where the Exchange Management Shell (EMS) session is running. If the mailbox specified via the -Mailbox parameter resides on a different server that does not support the dedicated Exchange hybrid app - but the EMS host server does - the ResultType still shows Success. This behavior is by design.
Auditing Exchange hybrid application usage in Entra ID
After configuring the dedicated Exchange hybrid application and enabling the feature on the Exchange Server, you can audit its usage through the Entra ID Sign-in logs. Follow these steps:
Log in to the Entra ID portal:
Navigate to the Entra ID portal and log in with your credentials.
Access Microsoft Entra ID:
In the portal, select or search for
Microsoft Entra ID.Navigate to Sign-in Logs:
In the navigation pane, go to
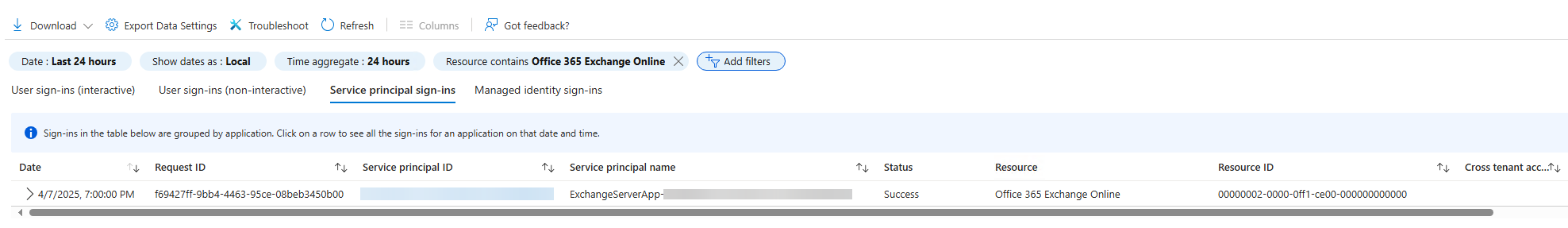
Monitoringand selectSign-in logs.View Service Principal Sign-ins:
Next, select
Service principal sign-insto view detailed logs.
The following picture illustrates a successful sign-in request:
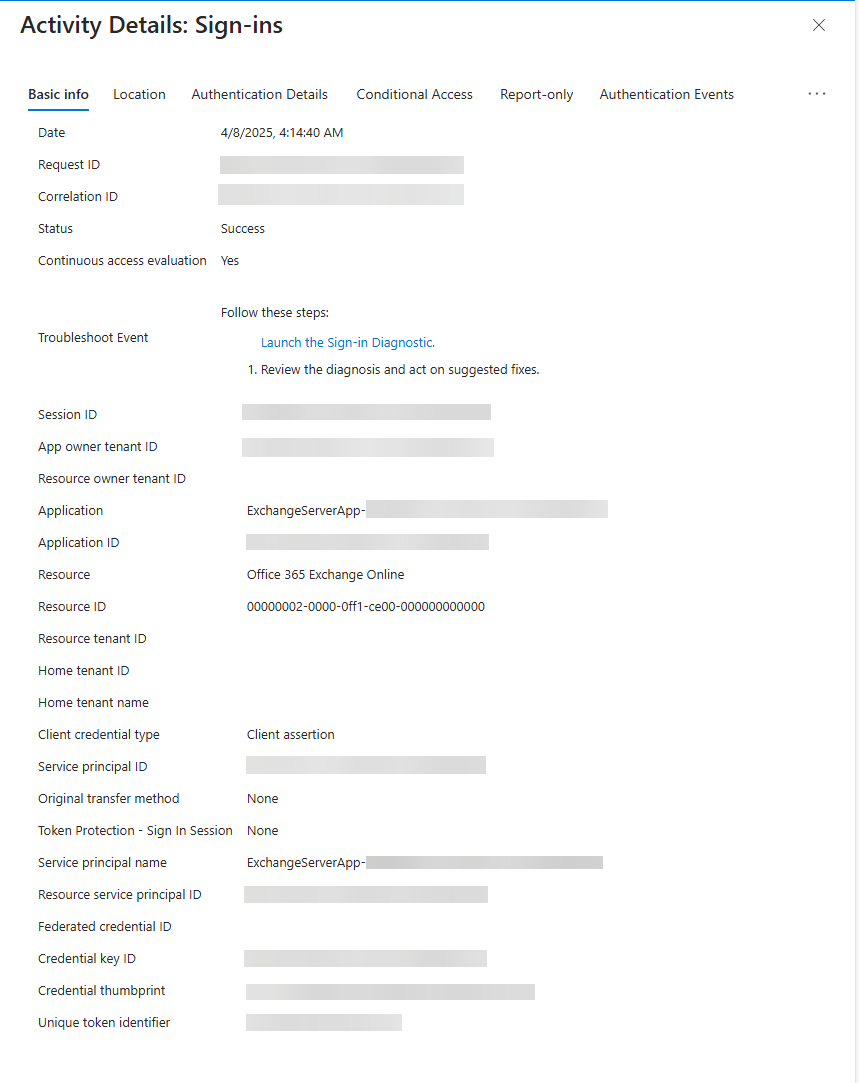
When you click on the entry, the Activity Details: Sign-ins flyout opens, providing more information about the sign-in activity:
Restrict access to dedicated Exchange hybrid application service principal
Some organizations may want to restrict access to the dedicated Exchange hybrid application service principal to a subset of public IP ranges used by Exchange Server. This can be achieved by utilizing Conditional Access for workload identities. This feature extends support for Conditional Access policies to service principals owned by the organization. Workload Identities Premium licenses are required to create or modify Conditional Access policies scoped to service principals. For more information, visit Microsoft Entra Workload ID.
How to enable the dedicated Exchange hybrid application feature via setting override
If you used the Hybrid Configuration Wizard (HCW) to configure the dedicated Exchange Hybrid application, you must run the New-SettingOverride cmdlet to enable the feature for your on-premises Exchange Server organization. Execute the following command from an elevated Exchange Management Shell (EMS):
New-SettingOverride -Name "EnableExchangeHybrid3PAppFeature" -Component "Global" -Section "ExchangeOnpremAsThirdPartyAppId" -Parameters @("Enabled=true") -Reason "Enable dedicated Exchange hybrid app feature"
Get-ExchangeDiagnosticInfo -Process Microsoft.Exchange.Directory.TopologyService -Component VariantConfiguration -Argument Refresh
How to roll back from dedicated Exchange hybrid application
Until the dedicated Exchange hybrid application becomes the default in HCW and EWS is deprecated for first-party applications, you can roll back the configuration applied by the ConfigureExchangeHybridApplication.ps1 script. A rollback should only be performed if you encounter issues after configuring the feature.
As a first step, run HCW to reconfigure the first-party Service Principal. Make sure to select the Oauth, Intra Organization Connector and Organization Relationship option, as this setting executes the necessary steps to reconfigure the first-party Service Principal.
Next, remove the Setting Override that enables the dedicated Exchange hybrid application feature. To do this, run the following command from an elevated Exchange Management Shell (EMS):
Get-SettingOverride | Where-Object {$_.ComponentName -eq "Global" -and $_.SectionName -eq "ExchangeOnpremAsThirdPartyAppId"} | Remove-SettingOverride
Get-ExchangeDiagnosticInfo -Process Microsoft.Exchange.Directory.TopologyService -Component VariantConfiguration -Argument Refresh
To revert the Auth Server change applied by the script, run the following command from an elevated Exchange Management Shell (EMS):
# Replace this id with the id of your tenant
$tenantId = "123e4567-e89b-12d3-a456-426614174000"
(Get-AuthServer | Where-Object {$_.Name -like "*evoSTS*" -and $_.Realm -eq $tenantId}) | Set-AuthServer -ApplicationIdentifier $null -DomainName $null
As a final step, you can use the ConfigureExchangeHybridApplication.ps1 script to delete the application that was created in Entra ID:
.\ConfigureExchangeHybridApplication.ps1 -DeleteApplication
Frequently Asked Questions
❓ Can we configure the dedicated Exchange hybrid app even if not all our servers are updated to the version that support it?
Yes, you can still configure and enable dedicated Exchange hybrid app. Servers on older versions of continue using the previous shared service principal workflow. Update all your servers before the new configuration becomes a requirement (October 2025). Once the dedicated app is created and enabled, as new servers are updated, they automatically start using the dedicated hybrid app.
❓ What happens if we re-run the Hybrid Configuration Wizard (HCW) after configuring the new dedicated Exchange hybrid app?
If you re-run HCW and you don't uncheck Oauth, Intra Organization Connector and Organization Relationship, the Auth Certificate is uploaded to the Exchange Online service principal of the shared Office 365 Exchange Online application, but your environment continues using the dedicated application created by the script because HCW does not modify the server settings override. If, however, you've used the script in Service Principal Clean-Up Mode to remove the key credentials of the shared service principal after configuring the dedicated Exchange hybrid app, re-running the HCW will re-upload the certificate to the shared service principal, and your need to run the clean up again.
❓ We have many Exchange servers in our organization. Does every server need a separate dedicated Exchange hybrid app?
Dedicated Exchange hybrid app is created in your tenant's Entra ID and needs to be configured only once per tenant. All your on-premises servers are able to use the same dedicated application (once they are updated to April 2025 HU or later).
❓ Does this change impact migration of mailboxes between Exchange Server and Exchange Online?
This change does not impact either onboarding or offboarding mailbox moves between Exchange Online and Exchange Server.
❓ Does this change impact any third-party applications connecting to Exchange Online mailboxes using EWS protocol?
This change impacts only Exchange hybrid EWS calls from on-premises servers to Exchange Online. Remember that there is a October 2026 deadline for Retirement of Exchange Web Services in Exchange Online.
❓ We have a multi-tenant hybrid organization (a single on-premises AD forest connected to multiple Exchange Online tenants). What do we have to do?
The script to switch to a dedicated Exchange hybrid app needs to be run once per tenant as it needs to update the corresponding Auth Server object and has to create the application in each of the tenants. The best approach is running the script in split execution mode to do all the configuration except creating the setting override (which enables Exchange Server to start using the new application). When all the tenants have the dedicated Exchange hybrid app created, run the script again to create the override and enable your on-premises Exchange servers to use the feature. More information can be found in the documentation.
❓ We have a multi-forest on-premises deployment connecting to a single Exchange Online hybrid tenant. What should we do?
The script should be run for each Exchange on-premises organization / forest. This action creates multiple dedicated hybrid apps in the single Microsoft 365 tenant, each named
ExchangeServerApp-{GUID of the Exchange organization}. In this scenario, you should not remove the certificate from the Shared Security Principal until all forests are ready (all servers are up to date) to work with their dedicated hybrid apps and the use of the dedicated app has been enabled in all forests.
❓ We have concerns with the dedicated Exchange hybrid app script assigning too many EWS permissions to the new dedicated application.
Once Exchange Server is updated to support Graph API calls for Exchange Hybrid - we update the script and direct our customers to re-run the script to remove the more permissive EWS permissions and replace them with more granular Graph API permissions. Note that the EWS permissions assigned in the first stage (creation of dedicated Exchange hybrid app before on-premises Graph API support is available) are the same as permissions that the shared security principal already has today.
❓ Why has Microsoft taken the direction of making customers create their own dedicated hybrid application instead of publishing a new application that is managed by Microsoft?
The approach of using a dedicated application in customer tenant gives customers more flexibility for future changes that may require modifications to the app. Consider the upcoming shift from EWS to Graph API calls: adjustments to the application are necessary (for example, updating API permissions). A dedicated customer application allows customers to choose when they want to transition from EWS API permissions to Graph API permissions. Since the dedicated application is automatically created and configured by the PowerShell script or (later this year) Hybrid Configuration Wizard, there is no added benefit for customers using a Microsoft managed application.
❓ Does it matter if an organization uses Modern or Classic Exchange hybrid configuration?
Changes mentioned in this blog post apply to both Modern (Hybrid Agent) or Classic Exchange hybrid.
❓ We've created the dedicated Exchange hybrid application and set the permissions as per the documentation. We then finished our migration and do not host any mailboxes on-premises so rich-coexistence is not required anymore. Anything we should do?
If you do not require the rich coexistence features anymore, you can run the script in
Delete Application Mode to delete the dedicated Exchange hybrid application and keep using Exchange on-premises for management or SMTP relay scenarios only. It's also strongly recommended to run the script in Service Principal Clean-Up Mode. Deleting the dedicated Exchange hybrid application doesn't revert the configuration changes done on the Exchange Server (on-premises) side. Follow the steps outlined in the documentation if you want to revert the configuration, too.
❓ We use Hybrid Modern Authentication (HMA). What is the guidance for us?
Currently, HMA uses the first-party (shared) service principal. Since it is not required to upload the Auth Certificate to the shared service principal when setting up HMA, this scenario remains unaffected by the change and continue functioning as before. Therefore, it is safe to remove the Auth Certificate from the shared service principal after switching to the dedicated Exchange hybrid application.
❓ We use Microsoft Entra Connect (previously Azure AD Connect) for directory synchronization. All our mailboxes are hosted on-premises. Is it necessary to create the dedicated Exchange hybrid application?
If you've never ran the Hybrid Configuration Wizard (HCW), there is no need to configure the dedicated Exchange hybrid application. However, if you ran HCW and intend to use hybrid features such as Free/Busy, MailTips, and profile picture sharing, creating the dedicated Exchange hybrid application is required.
❓ We have an Exchange hybrid setup but no on-premises mailboxes. We only use the server as an SMTP relay or recipient management. Do we need to create the dedicated Exchange hybrid application?
Creating the dedicated Exchange hybrid application is not required if you do not utilize hybrid features such as Free/Busy, MailTips, and profile picture sharing. To enable these hybrid features in the future, you need to configure the dedicated Exchange hybrid application.
❓ Our organization does not need rich coexistence and we just want to remove the certificate from the shared security principal. Do we need to install April HU first?
If all that you want to do is remove the certificate from the shared security principal and rich coexistence is not required, there is no dependency on installing the April 2025 before running the script. You can just run the script in the Service Principal Clean-Up Mode.
❓ We have Exchange hybrid setup for Microsoft Teams integration with on-premises mailboxes. Do we need to create a dedicated Exchange hybrid application or take any other action?
Creating the dedicated Exchange hybrid application is not required if all mailboxes are hosted on-premises. However, for environments where some mailboxes are hosted on-premises and others are hosted in Exchange Online, it's recommended to create the dedicated Exchange hybrid application. Doing so ensures that hybrid features such as Free/Busy, MailTips, and profile picture sharing continue to function properly.
❓ Can we rename the dedicated Exchange hybrid app from ExchangeServerApp-{Guid of the organization} to some other app name?
We recommend that administrators do not change the name of the app after it is created. Renaming the app could lead to the creation of a duplicate app in the future if the
ConfigureExchangeHybridApplication.ps1 script is re-run, for example, when renewing the Auth Certificate. The upcoming Hybrid Configuration Wizard (HCW) version that supports the dedicated Exchange hybrid application also uses the unique name of the app to detect whether it has already been created. Therefore, we do not recommend renaming the application in Entra ID.