Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
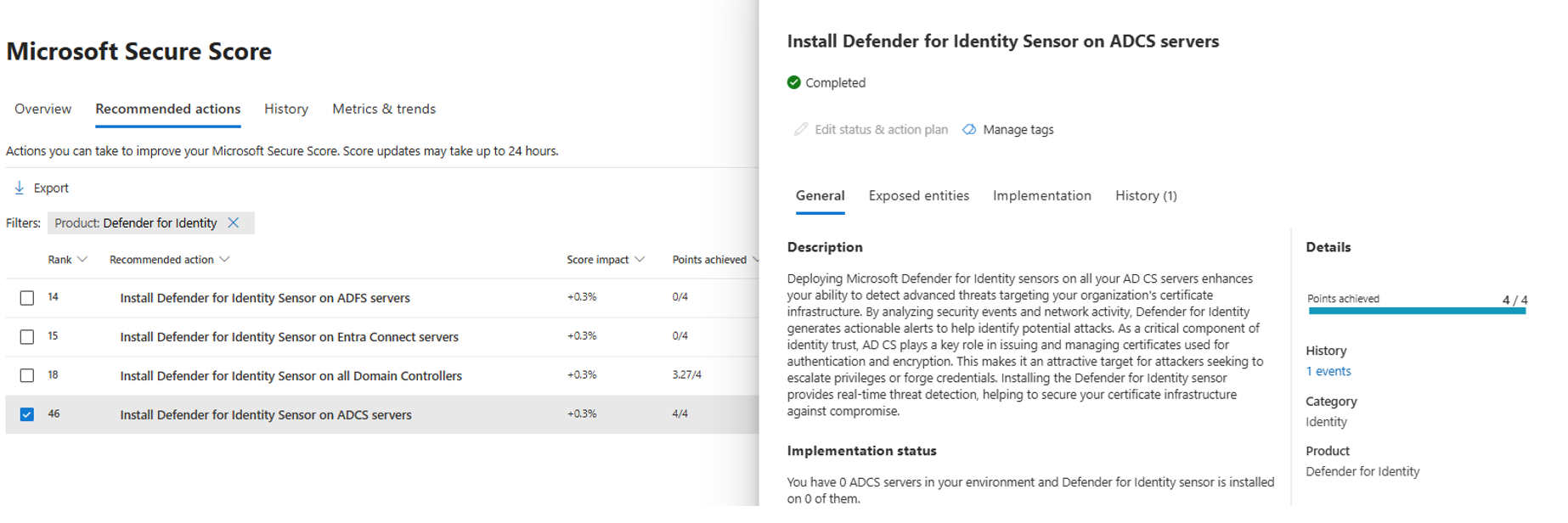
This article describes the security posture assessment report for unmonitored Active Directory Certificate Services (AD CS) servers by Microsoft Defender for Identity.
What risk do unmonitored ADCS servers pose to an organization?
Unmonitored Active Directory Certificate Services (AD CS) servers pose a significant risk to your organization’s identity infrastructure. AD CS, the backbone of certificate issuance and trust, is a high-value target for attackers aiming to escalate privileges or forge credentials. Without proper monitoring, attackers can exploit these servers to issue unauthorized certificates, enabling stealthy lateral movement and persistent access. Deploy Microsoft Defender for Identity version 2.0 sensors on all AD CS servers to mitigate this risk. These sensors provide real-time visibility into suspicious activity, detect advanced threats, and generate actionable alerts based on security events and network behavior.
Note
This security assessment is available only if Microsoft Defender for Endpoint detects an eligible AD CS server in the environment.
How do I use this security assessment?
Review the recommended action at https://security.microsoft.com/securescore?viewid=actions to discover which of your AD CS servers are unmonitored.
Go to the Microsoft Defender portal > Settings > Identities > Sensors. You can view the already installed sensors in your environment and download the install package to deploy them on your remaining servers.
Take appropriate action on those servers by configuring monitoring sensors.
Note
Assessment details update in near real time. However, scores and statuses refresh every 24 hours. The list of impacted entities updates within a few minutes of implementing recommendations, but the overall status might take longer to show as Completed.
Next steps
Learn more about Microsoft Secure Score.