Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to: ✔️ Linux VM ✔️ Windows VM ✔️ Generation 1 VM
Azure Virtual Machines supports upgrading Generation 1 virtual machines (VM) to Generation 2 by upgrading to the Trusted launch security type.
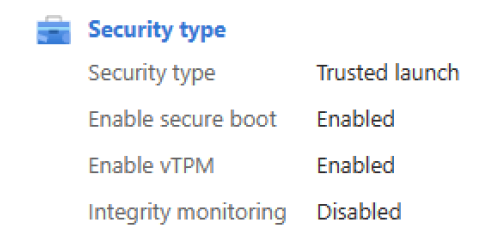
Trusted launch is a way to enable foundational compute security on Azure Generation 2 VMs and protects against advanced and persistent attack techniques like boot kits and rootkits. It does so by combining infrastructure technologies like Secure Boot, virtual Trusted Platform Module (vTPM), and boot integrity monitoring on your VM.
Note
Support for Upgrade of Gen1 VMs to Gen2 without enabling Trusted launch is not supported.
Prerequisites
- Azure VM is configured with:
- Trusted launch supported size family.
- Trusted launch supported operating system (OS) version (excluding Windows Server 2016, Debian, Azure Linux). For custom OS images or disks, the base image should be Trusted launch capable.
- Azure VM isn't using features currently not supported with Trusted launch.
- Azure Backup, if enabled, for VMs should be configured with the Enhanced Backup policy. The Trusted launch security type can't be enabled for VMs configured with Standard policy backup protection.
- Existing Azure VM backup can be migrated from the Standard to the Enhanced policy. Follow the steps in Migrate Azure VM backups from Standard to Enhanced policy.
- Upgrade a test Gen1 VM to Trusted launch and determine if any changes are required to meet the prerequisites before you upgrade Gen1 VMs associated with production workloads to Trusted launch.
- Disable any Windows OS volume encryption including BitLocker before upgrade if enabled. All Windows OS volume encryptions should be re-enabled post successful upgrade. This action isn't required for data disks or Linux OS volume.
Unsupported Gen1 VM configurations
Gen1 to Trusted launch VM upgrade is NOT supported if Gen1 VM is configured with:
- Operating system: Windows Server 2016, Azure Linux, Debian, and any other operating system not listed under Trusted launch supported operating system (OS) version. For Windows Server 2016 only, workaround is to update the Guest OS to Windows Server 2019 or 2022.
- VM size: Gen1 VM configured with VM size not listed under Trusted launch supported size families. As workaround, update the VM size to Trusted launch supported VM size family.
- Azure Backup: Gen1 VM configured with Azure Backup using Standard policy. As workaround, migrate Gen1 VM backups from Standard to Enhanced policy.
- BitLocker or equivalent encryption: Windows Gen1 VM guest OS volume is encrypted using BitLocker or equivalent encryption technology. As workaround, disable Windows OS volume encryption before upgrade and re-enable post successful completion of Trusted launch upgrade.
Best practices
Important
VM once upgraded to Trusted launch can't be rolled back to Gen1 configuration. It has to be fully recovered using Backup taken before upgrade.
- Take full backup OR Create restore points for Azure VMs associated with production workloads before you enable the Trusted launch security type. You can use the backup OR restore points to re-create the disks and VM with the previous Gen1 configuration well-known state.
- Review known issues and roll-back steps before executing Trusted launch upgrade.
- You won't be able to extend Windows OS disk system volume after
MBR to GPT conversionas part of upgrade. Recommendation is to extend system volume for future before upgrading to Trusted launch. - Windows OS disk volume should be defragmented using command
Defrag C: /U /V. Defragmentation of OS volume reduces the risk of MBR (Master boot record) to GPT (GUID partition table) conversion failure by freeing up end of partitions. Refer to defrag.
Update Guest OS volume
Generation 2 VMs requires guest OS volume with following configurations:
- GPT Disk layout: Guest OS volume of Gen1 VMs is mostly set to
MBRand requires to be updated toGPT - EFI system partition: Guest OS volume of Gen1 VMs mostly doesn't include this partition.
Complete the update of OS volume with required configuration before upgrading Azure Gen1 VM to Trusted launch.
Important
- Upgrade a test Gen1 VM to Trusted launch and determine if any changes are required to meet the prerequisites before you upgrade Gen1 VMs associated with production workloads to Trusted launch.
Using in-built MBR2GPT.exe utility, you can enable GPT disk layout AND add EFI system partition required for Gen2 upgrade.
Caution
You won't be able to extend Windows OS disk system volume after MBR to GPT conversion. Recommendation is to extend system volume for future before executing the upgrade.
Note
Windows Server 2016 doesn't support MBR2GPT.exe. Workaround is to update the Guest OS to Windows Server 2019 or 2022 and followed by MBR to GPT conversion. Refer to In-place upgrade for VMs running Windows Server in Azure.
Remotely connect (using RDP or command-line) to Gen1 Windows VM for executing conversion.
Run command
MBR2GPT /validate /allowFullOSand ensureDisk layout validationcompletes successfully. Do not proceed if theDisk layout validationfails. Refer to Known issues for list of common causes and associated resolution for failure. For more information and troubleshooting, see MBR2GPT troubleshooting.Run command
MBR2GPT /convert /allowFullOSto execute MBR to GPT conversion. Sample successful output:If conversion is successful the disk can only be booted in GPT mode. These changes cannot be undone! MBR2GPT: Attempting to convert disk 0 MBR2GPT: Retrieving layout of disk MBR2GPT: Validating layout, disk sector size is: 512 bytes MBR2GPT: Trying to shrink the OS partition MBR2GPT: Creating the EFI system partition MBR2GPT: Installing the new boot files MBR2GPT: Performing the layout conversion MBR2GPT: Migrating default boot entry MBR2GPT: Adding recovery boot entry MBR2GPT: Fixing drive letter mapping MBR2GPT: Conversion completed successfully MBR2GPT: Before the new system can boot properly you need to switch the firmware to boot to UEFI mode!
Upgrade Gen1 VM to Trusted launch
Note
- vTPM is enabled by default.
- Secure boot isn't enabled by default. We strongly recommend that you enable Secure Boot, if you aren't using custom unsigned kernel or drivers. Secure Boot preserves boot integrity and enables foundational security for VMs.
Make sure that you install the latest Azure PowerShell and are signed in to an Azure account with Connect-AzAccount.
Follow the steps to upgrade existing Gen1 VM to Gen2 and enable Trusted launch by using Azure PowerShell.
Sign in to the VM Azure subscription.
Connect-AzAccount -SubscriptionId 00000000-0000-0000-0000-000000000000Deallocate the VM.
Stop-AzVM -ResourceGroupName myResourceGroup -Name myVmEnable Trusted launch by setting
-SecurityTypetoTrustedLaunch.Get-AzVM -ResourceGroupName myResourceGroup -VMName myVm ` | Update-AzVM -SecurityType TrustedLaunch ` -EnableSecureBoot $true -EnableVtpm $trueValidate
securityProfilein the updated VM configuration.# Following command output should be `TrustedLaunch` (Get-AzVM -ResourceGroupName myResourceGroup -VMName myVm ` | Select-Object -Property SecurityProfile ` -ExpandProperty SecurityProfile).SecurityProfile.SecurityType # Following command output should return `SecureBoot` and `vTPM` settings (Get-AzVM -ResourceGroupName myResourceGroup -VMName myVm ` | Select-Object -Property SecurityProfile ` -ExpandProperty SecurityProfile).SecurityProfile.UefisettingsStart the VM.
Start-AzVM -ResourceGroupName myResourceGroup -Name myVmStart the upgraded Trusted launch VM. Verify that you can sign in to the VM by using either RDP (for Windows VMs) or SSH (for Linux VMs).
Roll back
Azure VM once upgraded to Trusted launch can't be rolled back to Gen1 configuration. You can disable Trusted launch to roll-back VM from Trusted launch to Gen2 (Non-Trusted launch) configuration.
Use the Backup or Restore point of Gen1 VM taken before upgrade and restore entire VM along with disks to roll back fully to Gen1 VM.
Known issues
VM image reference doesn't change post Trusted launch upgrade
Post upgrade of Azure Gen1 VM to Trusted launch, the image reference still reflects source as Gen1 OS image. Image reference not updated is a known limitation.
This limitation does not impacts the VM or hosted application functionality post Trusted launch upgrade. Following VM operations are impacted due to disconnect between image reference and running OS:
- Guest patching: For Server OS, Automatic guest patching installs updates based on the image reference of VM.
- Reimage: Reimaging VM using Gen1 image reference post Trusted launch upgrade will cause VM boot failure.
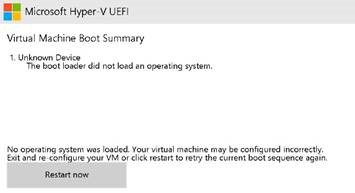
Windows 11 boot fails after Trusted launch upgrade of Windows 10 VM
Windows 10 Gen1 VM is successfully upgraded to Trusted launch followed by successful Windows 11 in-place upgrade. However, the Windows 11 boot fails after Azure VM is stopped and started with error shown.
Resolution: This issue is fixed with 24H2 build version 26100.2314 and 23H2 build version 22631.5624.
[Windows] MBR to GPT conversion fails with error Cannot find room for the EFI system partition
This error occurs for one of following reason:
- There's no free space available on the system volume
- System volume is corrupted. You can validate by trying to Shrink Volume by few MBs under Disk Management console. Use command
chkdsk C:/v/fto repair system volume. Virtual Diskservice isn't running or unable to communicate successfully. Service startup type should be set toManual.Optimize Drivesservice isn't running or unable to communicate successfully. Service startup type should be set toManual.- System volume disk is already configured with four MBR partitions (maximum supported by MBR disk layout). You need to delete one of the partitions to make room for EFI system partition.
- Run
ReAgentc /infoto identify partition actively used by Recovery. Example:Windows RE location: \\?\GLOBALROOT\device\harddisk0\partition4\Recovery\WindowsRE - Run PowerShell cmdlet
Get-Partition -DiskNumber 0to identify current partitions which are configured. - Run PowerShell cmdlet
Remove-Partition -DiskNumber 0 -PartitionNumber Xto remove any extra Recovery partition not actively used by Recovery service as identified in Step 1.
- Run
[Windows] MBR to GPT failed to update ReAgent.xml
For certain Windows OS versions like Windows 10, MBR2GPT generates pass-through error MBR2GPT: Failed to update ReAgent.xml, please try to manually disable and enable WinRE.
The warning indicates that MBR2GPT.exe was unable to update Recovery partition GUID in C:\Windows\System32\Recovery\ReAgent.xml. This issue shouldn't cause issue with Guest OS functionality or further upgrade operations like Windows 11 Upgrade to succeed or Windows 11 to work properly post Upgrade.
ReAgent.xml is updated with correct GUID post Windows 11 upgrade, that is, if you don’t take any action between MBR2GPT conversion & Windows 11 upgrade, the GUID value in ReAgent.xml is synced with Windows recovery configuration.
To manually fix The warning, you can disable and re-enable WinRE post MBR2GPT conversion or post Gen1 to Trusted launch upgrade before Windows 11 upgrade using listed steps, these steps forces sync the WinRE GUID in ReAgent.xml
- Complete Gen1 -> Trusted launch upgrade.
- Run
reagentc /disable - Run
reagentc /enable - Run
reagentc /info - Open
C:\Windows\System32\Recovery\ReAgent.xmland validate BCD GUID in xml file is matching the output from Step 4.
[Windows] D Drive assigned to System Reserved Post upgrade
Temporary storage Drive letter assignment 'D' is changed to 'E' with previous letter assigned to System Reserved post-upgrade of Gen1 VM. Execute below steps manually post-upgrade to work around the issue:
After the upgrade check the disks on the server, if system reserved partition has the letter D, do the following actions:
- Reconfigure pagefile from D: to C:
- Reboot the VM
- Remove letter D: from the partition
- Reboot the VM to show the temporary storage disk with D: letter
Frequently asked questions
What if there is Generation 1 VMs, that doesn't fit the prerequisites for Trusted launch?
For a Generation 1 VM that doesn't meet the prerequisites to upgrade to Trusted launch, look how to fulfill the prerequisites. For example, If using a virtual machine size not supported, look for an equivalent Trusted launch supported size that supports Trusted launch.
Why is upgrade to Generation 2 only (without Trusted launch) not supported?
Trusted launch enables foundational compute security on Azure Generation 2 VMs with no extra cost associated. Also, Trusted launch VMs are majorly on parity with Generation 2 VMs. Hence, there's no added benefit for upgrading only to Generation 2 VM without enabling Trusted launch.
Related content
- Refer to Deploy Trusted launch virtual machines for enabling Trusted launch on new virtual machine & scale set deployments.
- Refer to boot integrity monitoring for enabling boot integrity monitoring and monitor the health of the VM by using Microsoft Defender for Cloud.
- Learn more about Trusted launch and review frequently asked questions.