Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The audit log helps you investigate specific activities across Microsoft services. Microsoft Sentinel data lake activities are audited and can be searched in the audit log. The audit log provides a record of activities that are performed by users and administrators in Microsoft Sentinel data lake, such as:
- Accessing data in lake via KQL queries
- Running notebooks on data lake
- Create/ edit/ run/ delete jobs
Auditing is automatically turned on for Microsoft Sentinel data lake. Features that are audited are logged in the audit log automatically.
Prerequisites
Microsoft Sentinel data lake uses the Microsoft Purview auditing solution. Before you can look at the audit data, you need to turn on auditing in the Microsoft Purview portal. For more information, see Turn auditing on or off.
To access the audit log, you need to have the View-Only Audit Logs or Audit Logs role in Exchange Online. By default, those roles are assigned to the Compliance Management and Organization Management role groups.
Note
Global administrators in Office 365 and Microsoft 365 are automatically added as members of the Organization Management role group in Exchange Online.
Important
Global Administrator is a highly privileged role that should be limited to scenarios when you can't use an existing role. Microsoft recommends that you use roles with the fewest permissions. Using accounts with lower permissions helps improve security for your organization.
Microsoft Sentinel data lake activities
For a list of all events that are logged for user and admin activities in Microsoft Sentinel data lake, see the following articles:
- Microsoft Sentinel data lake onboarding activities
- Microsoft Sentinel data lake notebook activities
- Microsoft Sentinel data lake job activities
- Microsoft Sentinel data lake KQL activities
For detailed audit log schema information, see Microsoft Sentinel data lake schema.
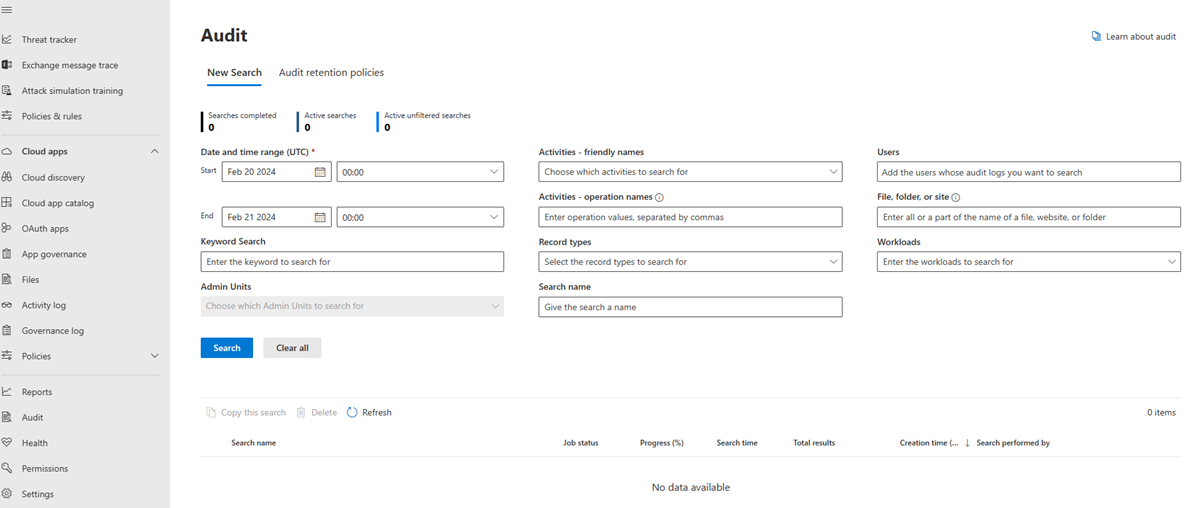
Search the audit log
Follow these steps to search the audit log:
Navigate to the Microsoft Purview portal and select Audit.
On the New Search page, filter the activities, dates, and users you want to audit.
Select Search
Export your results to Excel for further analysis.
For step-by-step instructions, see Search the audit sign in the Microsoft Purview portal.
Audit log record retention is based on Microsoft Purview retention policies. For more information, see Manage audit log retention policies.
Search for events using a PowerShell script
You can use the following PowerShell code snippet to query the Office 365 Management API to retrieve information about Microsoft Defender XDR events:
$cred = Get-Credential
$s = New-PSSession -ConfigurationName microsoft.exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $cred -Authentication Basic -AllowRedirection
Import-PSSession $s
Search-UnifiedAuditLog -StartDate 2023/03/12 -EndDate 2023/03/20 -RecordType <ID>
Note
See the API column in Audit activities included for the record type values.
For more information, see Use a PowerShell script to search the audit log