Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Boards and Azure Pipelines now support integration with GitHub Enterprise Cloud organizations with data residency enabled. You can learn more about how to create a new connection for Azure Boards and a new pipeline from the release notes.
In addition, with this release we are no longer allowing organizations to create public projects. This change won't impact organizations that already have the Allow public policy enabled.
Check out the release notes for details.
GitHub Advanced Security for Azure DevOps
- New secret patterns added to Advanced Security
- Periodic repository re-scans performed for secret scanning
- Dismissals in Advanced Security now available in alert detail UI
- Validity checking for secrets now generally available
General
- Only organizations with existing public projects can create new ones
- Azure DevOps login flow no longer relies on Azure Resource Manager audience
- Continuous Access Evaluation on Azure DevOps
Azure Boards
Azure Repos
- Improved screen reader support for pull request experience
- Azure DevOps remote index support in VSCode
GitHub Advanced Security for Azure DevOps
New secret patterns added to Advanced Security
New patterns have been added to Advanced Security's Secret Protection for both user alerts and push protection. View the updated list of supported secret patterns at Secret scanning patterns.
Periodic repository re-scans performed for secret scanning
For any stale repositories, without committing to the repository you may not receive alerts for new or updated secret patterns. To resolve this, we've added periodic, automatic re-scans performed on your behalf to raise new alerts for updated patterns.
Dismissals in Advanced Security now available in alert detail UI
Previously, dismissal information was only available via the alerts API. Now, information about the latest dismissal and the user identity shows up in the alert detail view.
This address Developer Community feedback.
Validity checking for secrets now generally available
Validity checking is a feature to determine if an exposed secret is active or inactive, helping you prioritize your remediation efforts. No opt-in is needed; once the feature is available in your organization, any patterns that support validity checking will automatically attempt a validity check. In an alert that supports validity checking, you can also manually re-validate the secret.
See all supported patterns with validity checking at Secret scanning patterns.
General
Only organizations with existing public projects can create new ones
Starting this sprint, only organizations that already have the Allow public projects policy enabled can continue using it. The policy does not change for existing customers.
Microsoft recommends using GitHub for all your public project needs.
Azure DevOps login flow no longer relies on Azure Resource Manager audience
We've removed a dependency on the Azure Resource Manager (ARM) resource (https://management.azure.com) when logging in or refreshing Entra access tokens used to access Azure DevOps. The ARM resource is often associated with the Azure portal (https://portal.azure.com), and admins may want to restrict which users in their tenant can access the portal through Conditional Access policy (CAP) enforcement.
Due to Azure DevOps previous reliance on ARM, admins had to permit all Azure DevOps users to bypass the ARM CAPs in order to use Azure DevOps. This is no longer necessary as we've removed the ARM resource audience requirement during signin and refresh token flows.
There remain a couple of notable exceptions — the following user groups may need continued access to ARM:
- Billing admins need access to ARM to setup billing and access subscriptions
- Service Connection creators require continued access to ARM for ARM role assignment and updates to MSIs
Continuous Access Evaluation on Azure DevOps
Azure DevOps now supports Continuous Access Evaluation (CAE), enabling near real-time enforcement of Conditional Access policies through Microsoft Entra ID. This enhancement allows Azure DevOps to instantly revoke access when critical events occur—such as user disablement, password resets, or location/IP changes—without waiting for token expiration. Real-time enforcement means that compromised accounts or policy violations are addressed as soon as we learn of the event, reducing exposure windows and improving incident response. Developers using CAE-capable client libraries ([].NET now available](https://www.nuget.org/packages/Microsoft.TeamFoundationServer.Client/20.259.0-preview), Python and Go to come) must handle claims challenges and update sign-in flows accordingly. General availability begins August 2025 following phased rollout for all customers.
Azure Boards
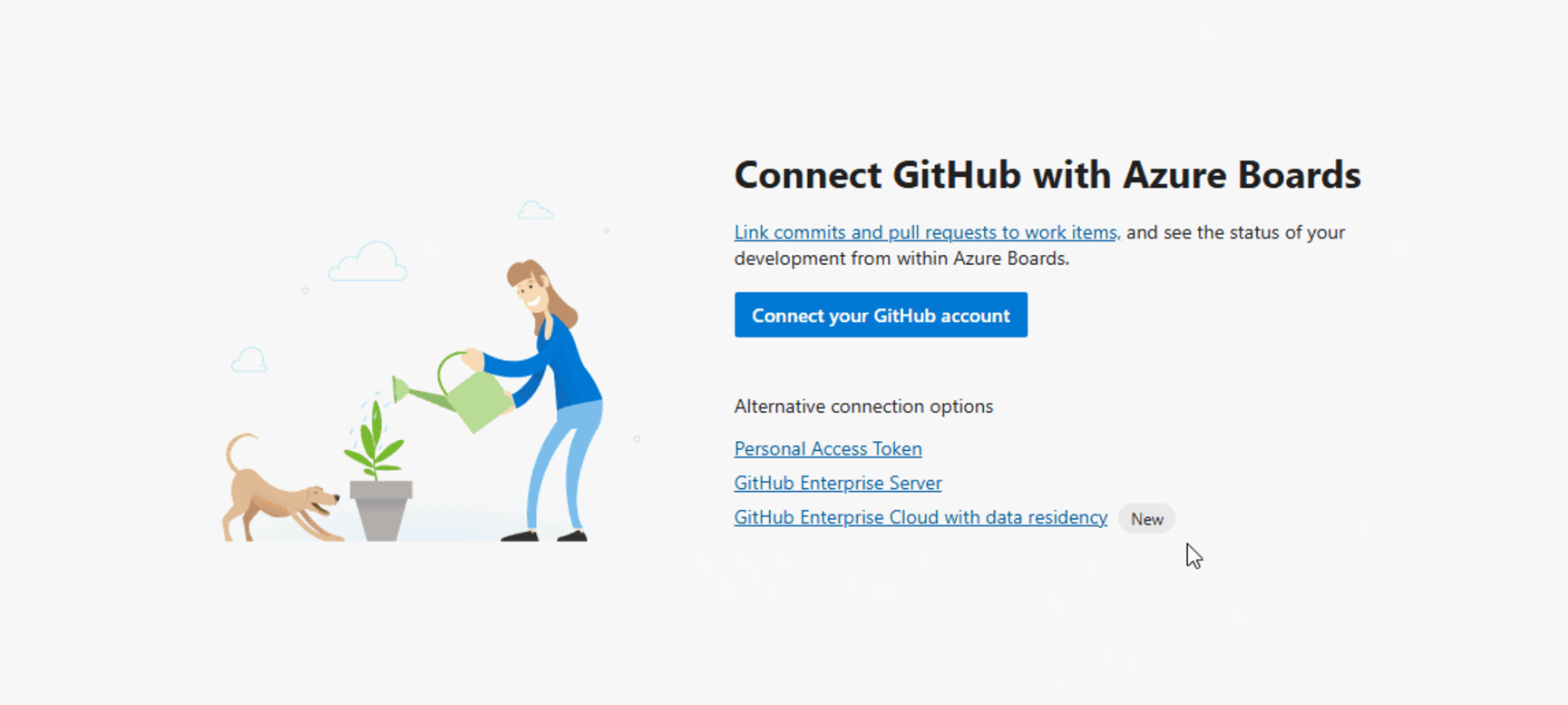
Azure Boards and Pipelines integration for GitHub Enterprise Cloud with Data Residency
Azure Boards and Azure Pipelines now supports integration with GitHub Enterprise Cloud organizations that have data residency enabled. This update aligns with GitHub’s September 2024 announcement introducing data residency for Enterprise Cloud customers.
To connect an Azure Boards project:
Create a new connection in Azure Boards. Then select the GitHub Enterprise Cloud with data residency option.
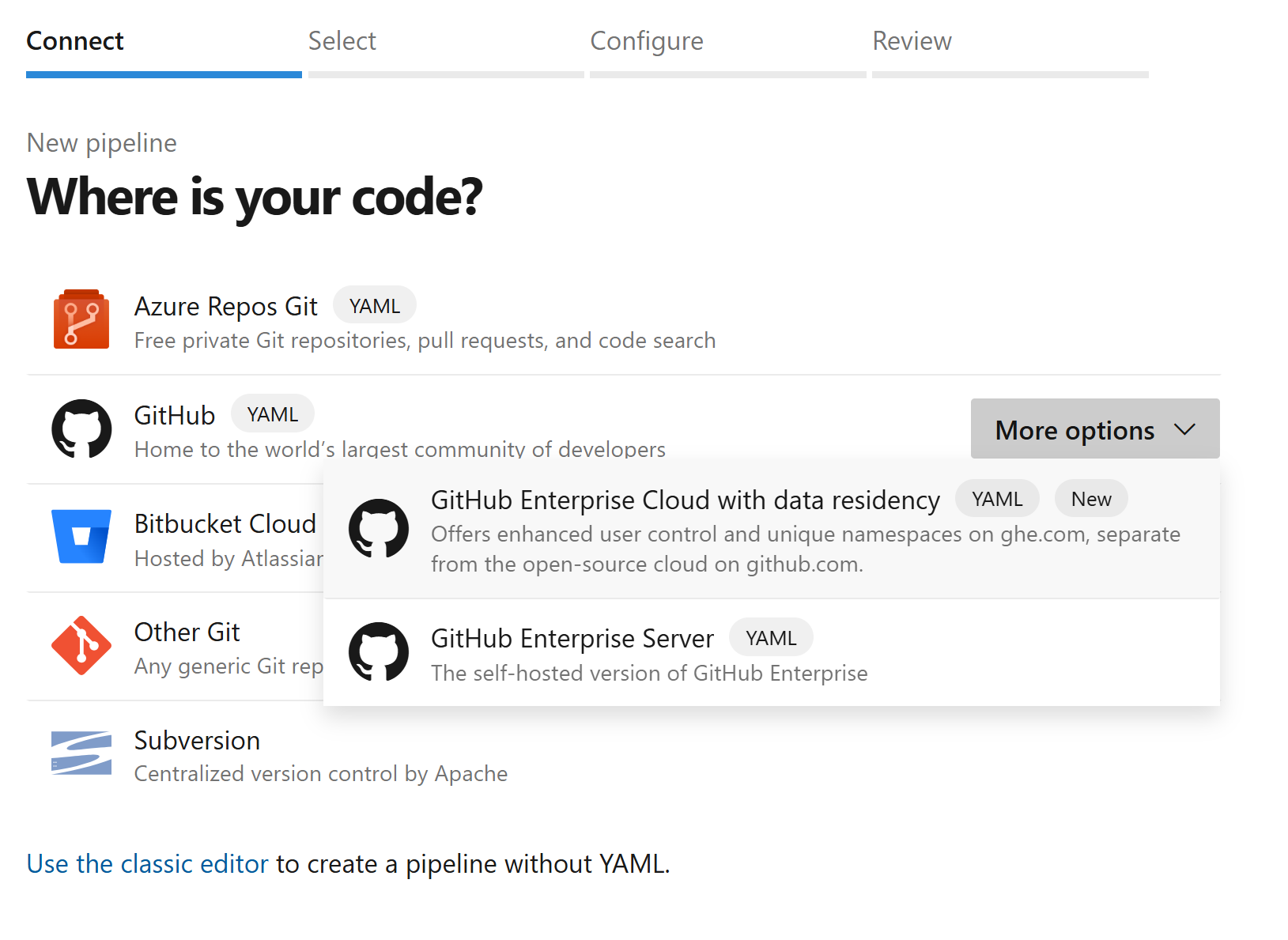
To connect an Azure Pipeline:
Create a new Pipeline and select GitHub > More Options > GitHub Enterprise Cloud with data residency.
Then enter the URL of your GitHub Enterprise Cloud organization.
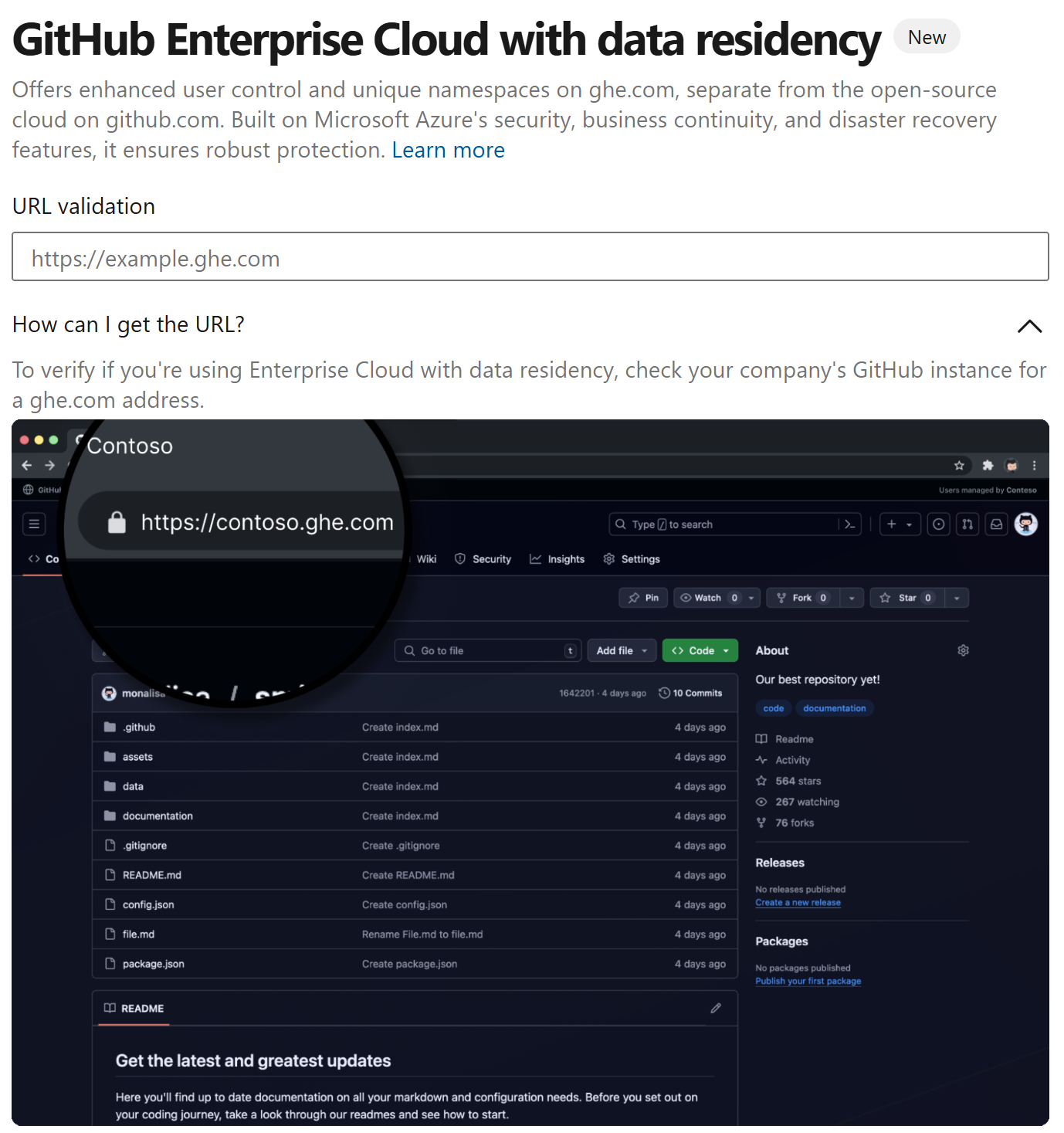
After your https://organization.ghe.com url is validated, the experience is same as it has always been, and you can select your GitHub repositories.
Azure Repos
Improved screen reader support for pull request experience
We improved support for screen readers in the pull request experience. The new option in built-in code editor will let you enable announcements for line changes and comments.
To enable the new option, from the pull request page click on the File tab.
Then, click on the Editor preferences button.
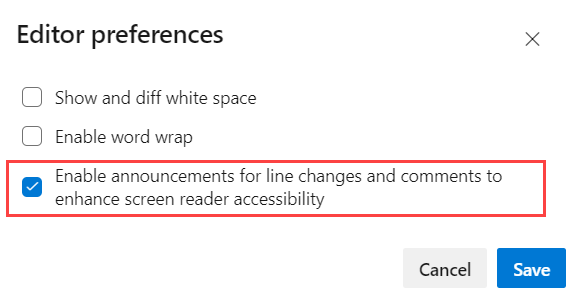
On the popup menu, select the Enable announcements for line changes and comments to enhance screen reader accessibility option and Save.
Azure DevOps remote index support
Azure DevOps now supports remote indexes for IDE workspaces that are linked to Azure DevOps repos. This enables #codebase to search for relevant snippets almost instantly without any initialization. This even works for larger repos with tens of thousands of indexable files. Support for remote workspaces has released starting with the July updates to Visual Studio and VS Code. For more info please see the VS Code Release Notes.
Remote indexes are used automatically when working in a workspace that is linked to Azure DevOps through git. Make sure you are also logged into Visual Studio or VS Code with the Microsoft account you use to access the Azure DevOps repo.
Next steps
Note
These features will roll out over the next two to three weeks. Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.