Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article shows you how to create tenant level service health alerts in the Azure portal and provides some troubleshooting guidance.
Note
Service Health events may be scoped at either the tenant level or the subscription level, depending on the nature of the event. To ensure full visibility into all relevant events, we recommend configuring alert rules at both levels.
Use the Azure service health page
In the Azure portal, navigate to Monitor > Service Health.
Select Create service health alert. A context pane opens.
Under Scope, select the Scope level as Directory. The current directory is displayed.
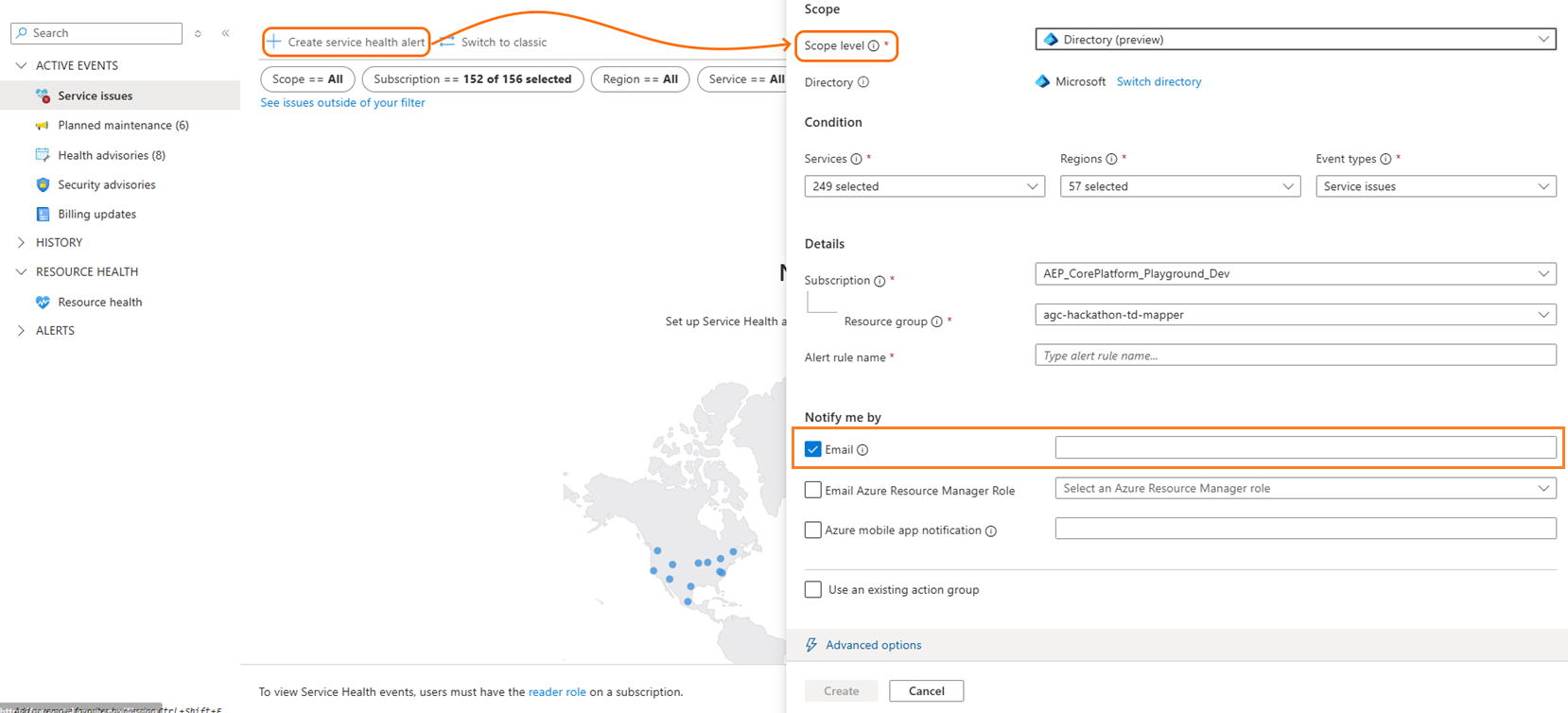
Under the Condition section, select the services, regions, and event types you’re interested in monitoring.
Under the Details section, name the alert rule and select where to save it.
Use the alert rule creation wizard
In the Azure portal, navigate to Monitor > Alerts.
Select Create > Alert rule. The alert rule creation wizard opens.
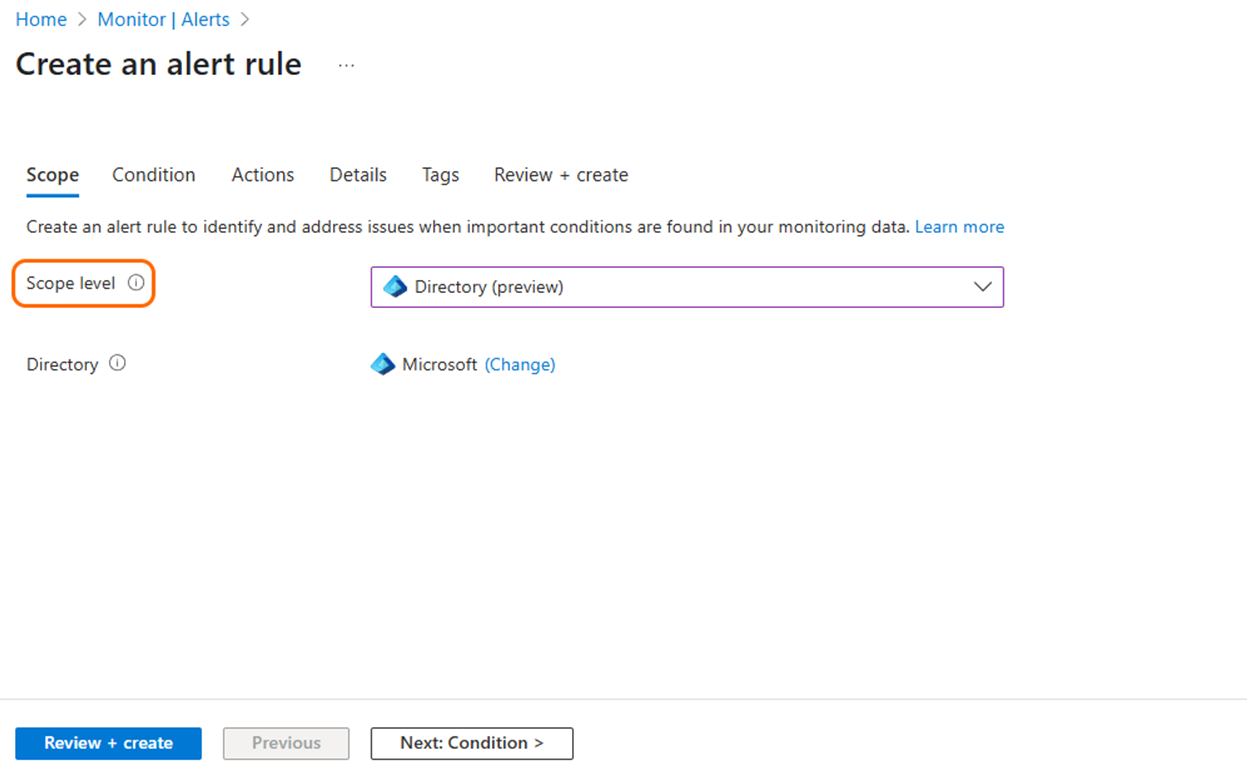
In the Scope tab, select the Scope level as Directory. The current directory is displayed.
In the Condition section, select the services, regions, and event types you’re interested in monitoring.
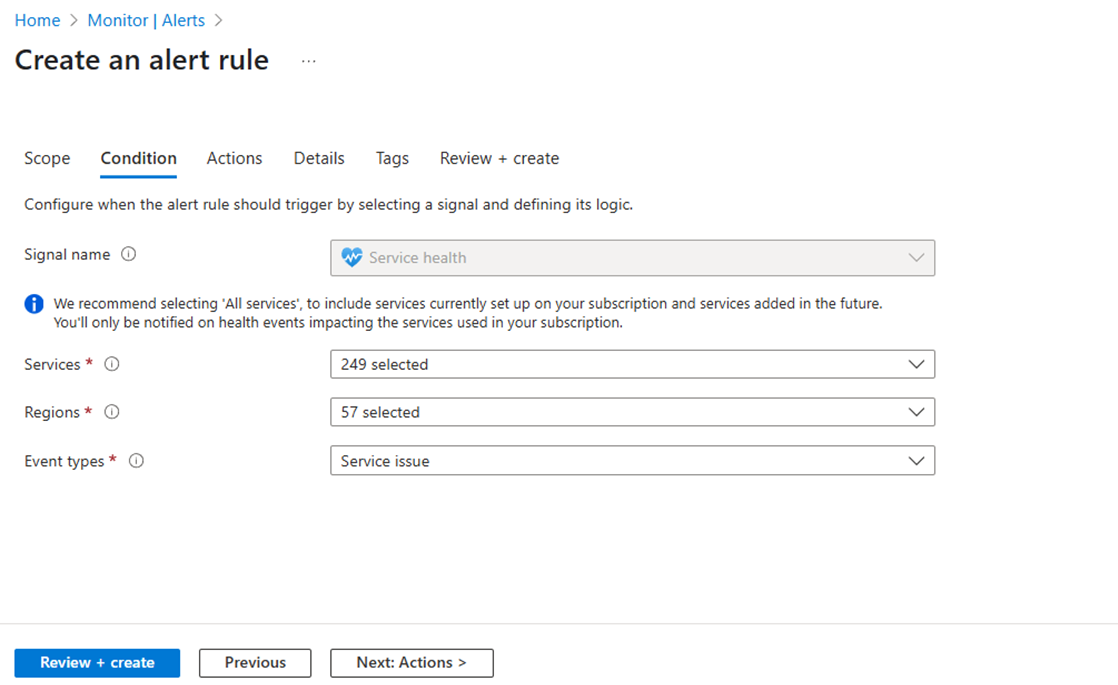
Continue creating the alert rule.
Troubleshoot
No permissions to create the tenant-level SH alert rule
To create an alert rule that monitors tenant-level Service Health events, the user must have Read access to tenant data. Such access can be granted when the user is associated with a Microsoft Entra role, as indicated here: Roles with tenant admin access - Azure Service Health | Microsoft Learn
When attempting to create a tenant-level SH alert rule without the required permissions, the user gets an unauthorized error message:
❗ Create alert rule
Failed to create alert rule. Error: StatusCode=Forbidden, ReasonPhrase=Forbidden, responseContent={"error":{"code":"AuthorizationFailed","message":"The client '00000000-0000-0000-000000000000' with object id '00000000-0000-0000-000000000000' does not have authorization to perform action 'Microsoft.ResourceHealth/events/read' over scope '/providers/Microsoft.ResourceHealth' or the scope is invalid. If access was recently granted, please refresh your credentials."}} Activity ID: 00000000-0000-0000-000000000000.
Recommendation
Make sure the user attempting to create the alert rule has tenant admin access. If the user lacks the necessary permissions, they'll receive a 'No access' result and should consult their subscription owner for the being granted access.
Fired tenant-level SH alerts aren’t shown in the alerts list
With this release, alerts fired on tenant-level SH events aren't shown in the alerts list.
Any actions associated with the alert rule (for example, email, webhook) contain a link to view the tenant-level event in the Azure Service Health portal page when a tenant-level SH alert fires.
In the following example, the alert email contains a link to view the event in the Service Health page, unlike other alert emails that contain a link to view the alert details.
Recommendation
Users should open the Service Health page in the portal to view tenant-level events.
A tenant-level SH alert rule didn’t fire on subscription-level events
Tenant-level Service Health events only cover tenant related issues. That means users shouldn’t expect to get both a tenant-level and subscription-level SH alerts for the same problem.
Recommendation
Create separate alert rules with different scopes:
- A Service Health alert rule scoped to the tenant
- A Service Health alert rule scoped to the subscription. A separate alert rule is required for each subscription that customer would like to monitor.