Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
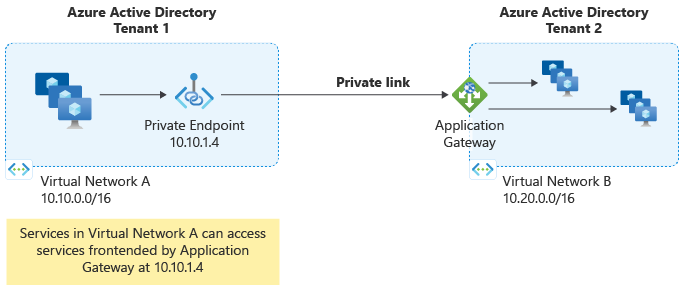
Azure Application Gateway Private Link enables you to establish secure, private connections to your Application Gateway from workloads spanning across virtual networks (VNets) and subscriptions. This feature provides private connectivity without exposing traffic to the public internet. For more information, see Application Gateway Private Link.
Configuration options
You can configure Application Gateway Private Link using multiple methods:
- Azure portal
- Azure PowerShell
- Azure CLI
Prerequisites
Before configuring Private Link, ensure you have:
- An existing Application Gateway
- A virtual network with a dedicated subnet for Private Link (separate from the Application Gateway subnet)
- Appropriate permissions to create and configure Private Link resources
Define a subnet for Private Link configuration
To enable Private Link configuration, you must create a dedicated subnet that's separate from the Application Gateway subnet. This subnet is used exclusively for Private Link IP configurations and can't contain any Application Gateway instances.
Subnet sizing considerations:
- Each IP address allocated to this subnet supports up to 65,536 concurrent TCP connections through Private Link
- To calculate required IP addresses:
n × 65,536connections, wherenis the number of IP addresses provisioned - Maximum of eight IP addresses per Private Link configuration
- Only dynamic IP address allocation is supported
Important
The combined length of the Application Gateway name and Private Link configuration name must not exceed 70 characters to avoid deployment failures.
To create a dedicated subnet for Private Link, see Add, change, or delete a virtual network subnet.
Configure Private Link
The Private Link configuration defines the infrastructure that enables connections from Private Endpoints to your Application Gateway. Before creating the Private Link configuration, ensure that a listener is actively configured to use the target frontend IP configuration.
Follow these steps to create the Private Link configuration:
- Navigate to the Azure portal.
- Search for and select Application Gateways.
- Select your Application Gateway instance.
- In the left navigation pane, select Private link, then select + Add.
- Configure the following settings:
- Name: Enter a name for the Private Link configuration
- Private link subnet: Select the dedicated subnet for Private Link IP addresses
- Frontend IP Configuration: Select the frontend IP configuration that Private Link should forward traffic to
- Private IP address settings: Configure at least one IP address
- Select Add to create the configuration.
- From your Application Gateway settings, copy and save the Resource ID. This identifier is required when setting up Private Endpoints from different Microsoft Entra tenants.
Configure Private Endpoint
A Private Endpoint is a network interface that uses a private IP address from your virtual network to connect securely to Azure Application Gateway. Clients use the Private Endpoint's private IP address to establish connections to the Application Gateway through a secure tunnel.
To create a Private Endpoint, follow these steps:
- In the Application Gateway portal, select the Private endpoint connections tab.
- Select + Private endpoint.
- On the Basics tab:
- Configure the resource group, name, and region for the Private Endpoint
- Select Next: Resource >
- On the Resource tab:
- Verify the target resource settings
- Select Next: Virtual Network >
- On the Virtual Network tab:
- Select the virtual network and subnet where the Private Endpoint network interface will be created
- Select Next: DNS >
- On the DNS tab:
- Configure DNS settings as needed
- Select Next: Tags >
- On the Tags tab:
- Optionally add resource tags
- Select Next: Review + create >
- Review the configuration and select Create.
Important
If the public or private IP configuration resource is missing when trying to select a Target sub-resource on the Resource tab of private endpoint creation, ensure a listener is actively utilizing the respected frontend IP configuration. Frontend IP configurations without an associated listener can't be shown as a Target sub-resource.
Note
When provisioning a Private Endpoint from a different Microsoft Entra tenant, you must use the Azure Application Gateway Resource ID and specify the frontend IP configuration name as the target sub-resource.
For example, if your private IP configuration is named PrivateFrontendIp in the portal, use PrivateFrontendIp as the target sub-resource value.
Caution
When moving a Private Endpoint to a different subscription, you must first delete the existing connection between the Private Link and Private Endpoint. After deletion, create a new Private Endpoint connection in the target subscription to reestablish connectivity.
Next steps
To learn more about Azure Private Link and related services: