Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Recently, I came across a situation while working with one of our customers for implementing their PKI Infra – I thought it would be worth to share it with you guys, let’s start talking about it without any delay!
Scenario:
Our customer has AD-CS deployed for the sake of issuing digital certificates for users, machines and servers – they had some business-critical servers which were receiving SSL connections from third parties/partners which are not managed by our customers – as you might be aware the, any client which makes SSL connection to servers, by design would “validate” the presented certificate. As a part of the validation process client may have to download “Certificate Revocation List” – this can be understood as the list of black listed certificates which will be generated, digitally signed by the from the “Certificate Authority”
In this case we had to make sure that, “CRL Distribution Point” aka CDP, is reachable by clients at the partner sites and they can download CRLs without any issues – CDPs can be over HTTP or LDAP – while both methods have its own pros and cons.
There are number of ways to create a HTTP based CDP and allow anonymous access – so that clients can download CRL without being authenticated, – HOWEVER in this case we wanted to make sure LDAP based CDP point is available for client apps/machines at the partner site because of some compatibility reasons.
This means, that we might have to allow anonymous access to the below LDAP location which has the CRL in it.
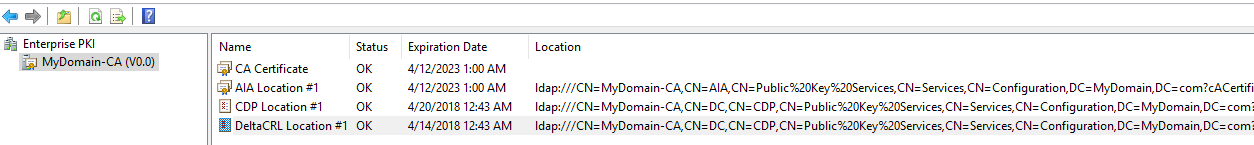
Below is the default location of the LDAP based CDP – which gets created while AD-CS role is being installed.
#1 ldap:///CN=MyDomain-CA,CN=DC,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=MyDomain,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
Can we just go-ahead and allow anonymous access to above said location right away?? – Unfortunately, the answer is NO
Our customers were not happy to share the server names’ outside network for obvious reasons like anyone else and we had to change the default location for few other reasons.
* (please note that, I have URLs and screenshots from my lab environment)*
Below is the default LDAP url that’s part of ADCS setup è this instructs AD-CS to publish the CRL to #1
ldap:///CN=<CATruncatedName><CRLNameSuffix>,CN=<ServerShortName>,CN=CDP,CN=Public Key Services,CN=Services,<ConfigurationContainer><CDPObjectClass>
And this is where it gets interesting.
So, what we need to do is:
- Change the default location of CDP to a new LDAP location – which doesn’t have any server names in its DN.
- Configure AD-CS to write the CRL to new CDP location, every time in creates one.
- Allow “Anonymous Access” just to the new LDAP location.
- Verify anonymous access to the new location using ldp.exe.
I will walk you through this.
Step 1) Change the default location of CDP to a new LDAP location – which doesn’t have any server names in its DN – Or to any location if needed.
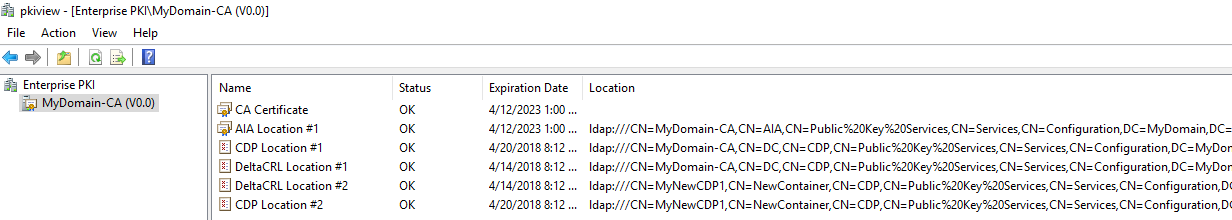
- Before we start, below is the view of pkiview.msc showing the CDP and delta CRL’s default location under “Configuration Partition”
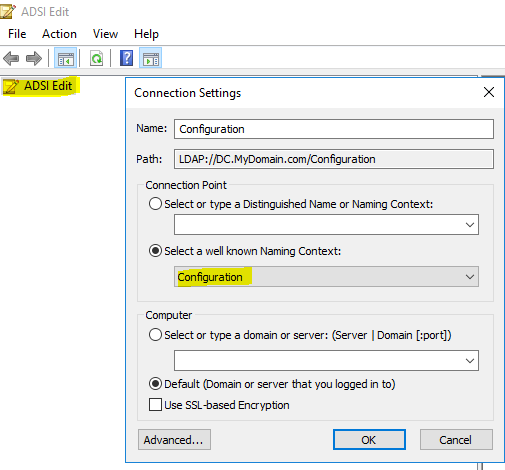
- To change this, we will have to create a new “cRLDistributionPoint” class object under CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,CN=MyDomain,DC=Com
- Navigate it to CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,CN=MyDomain,DC=Com
- Right click on the middle pane and click : New à Create Object à Select ‘Container’ class – though it’s possible to just rename default container with the DC name, we chose to add a new container and modify the new one – as this will give us an opportunity to fall back to the default configuration should something go wrong.
- Double click on the new ‘Container’ and create new object with ‘cRLDistributionPoint’ class and name it to whatever you want.
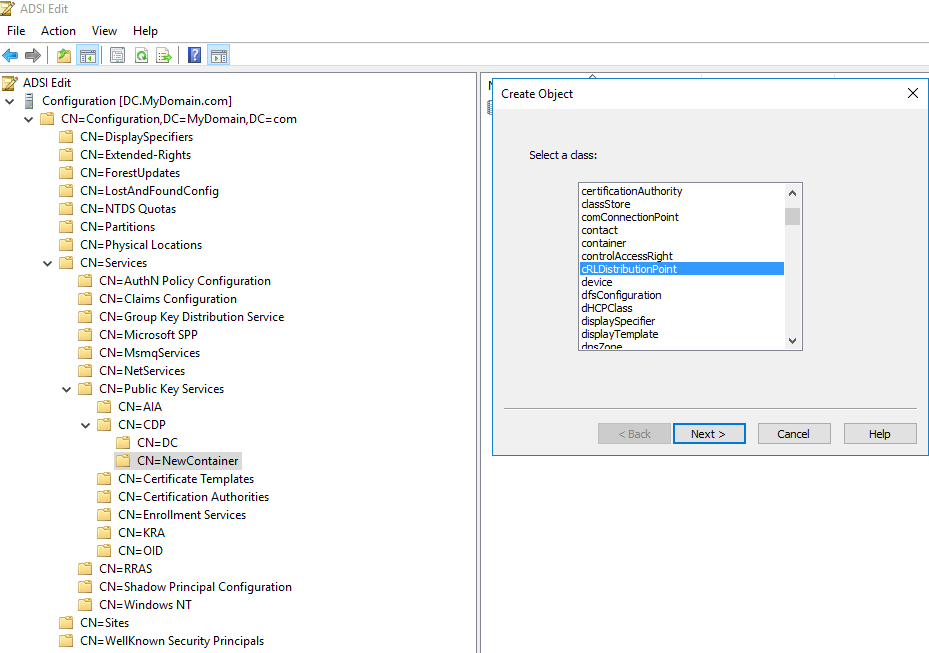
- I have the names as ‘NewContainer’ and ‘MyNewCDP1’
- So, you should have the newly created object’s DN something like CN=MyNewCDP1,CN=NewContainer,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=MyDomain,DC=com
Step 2) Configure AD-CS to write to the new CDP location every time it generates a new CRL.
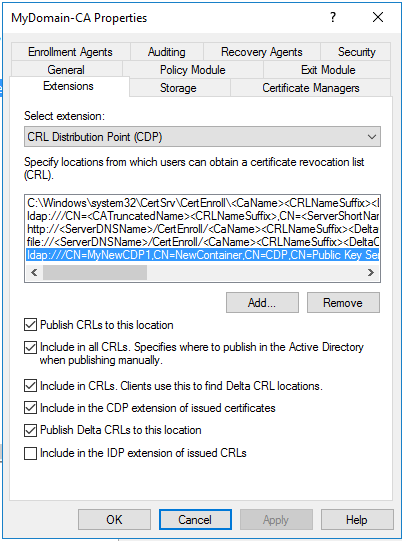
- Open up “Certificate Authority” à Right click on the node’s name à properties à Extensions tab
- Make sure you have “CRL Distribution Point (CDP)” under ‘Select extension’
- Click on “Add” and type in the following text in the resulting text box
ldap:///CN=MyNewCDP1,CN=NewContainer,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=MyDomain,DC=com<CDPObjectClass>
- Click on the appropriate checkboxes, so that it looks like below
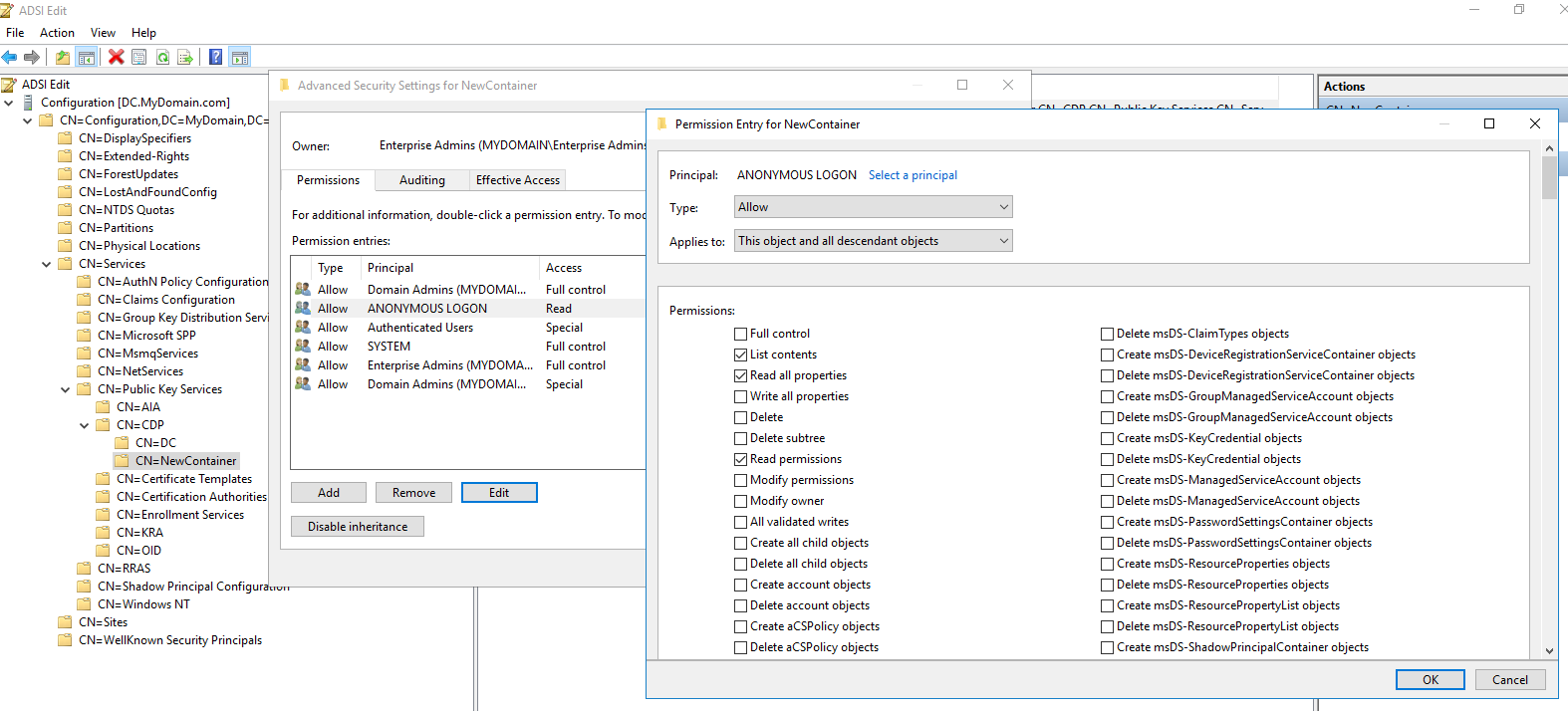
Step 3) Allow “Anonymous Access” just to the new LDAP location:
- To allow Anonymous Binding, at forest level:
- Connect to “Configuration Partition”, navigate it to CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=MyDomain,DC=com
- Right click on “CN=Directory Service” and navigate it to properties.
- Change the attribute “dSHeuristics” to “0000002” – It should be 0000000 for most of the installations, however if you have any other values just set the last digit to ‘2’ without modifying other values.
- Once done, set ACL on the object itself, where you want Anonymous access.
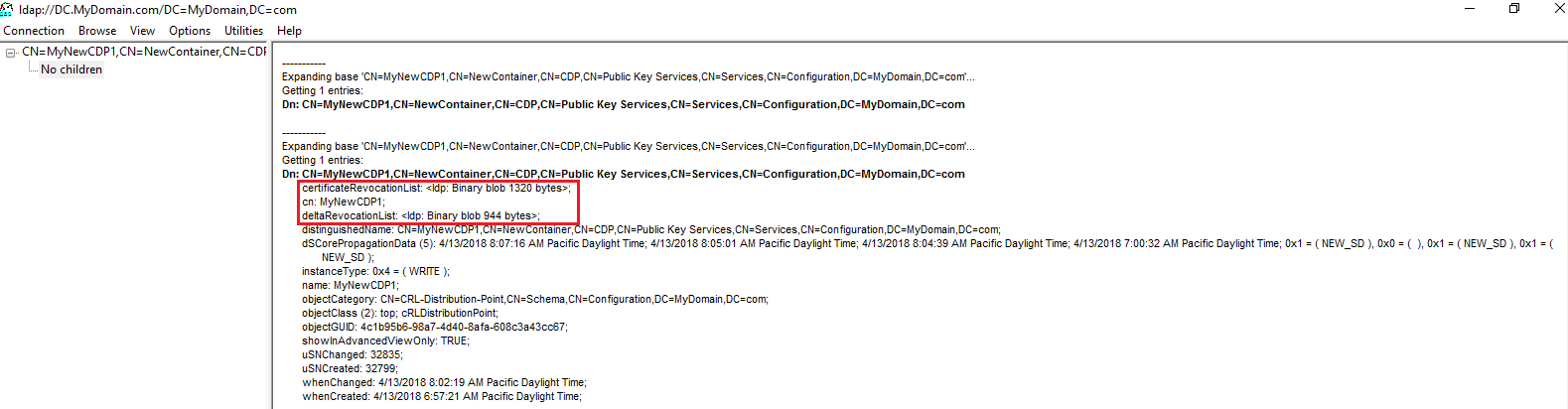
Step 4) Verify anonymous access to the new location using ldp.exe.
- We should be able to comfortably test this using ldp.exe
- Connect to your domain
If you can see a message like above, then you are good to go!
Hope this helps!